Active Directory (AD) is a structure used on computers and servers running the Microsoft Windows operating system (OS). AD is used to store network, domain, and user information and was originally created by Microsoft in 1996. It was first deployed on Microsoft Windows 2000. Active directories provide a number of functions to include providing information regarding objects optimized for fast access and / or retrieval. This allows administrators to setup security, push computer updates, and acts as a hierarchical structure. The structure is normally configured in three categories to include: hardware such as printers or scanners, web email servers, and objects that are the network and domain’s main functions.
What Are Active Directories Used to Do?
Active Directory is used by computer administrators to manage end user computer software packages, files, and accounts on medium to large-sized organizations. Instead of visiting every single computer client computer to upgrade new software or install Windows patches, the task(s) can be accomplished through updated a single object located within an AD forest or tree. Similarly, AD gives the network administrator the capability to grant or remove access at the user level for one or many applications or file structures. The two types of “trusts” that are incorporated into Microsoft Active Directory are one way non-transitive and transitive trusts. In transitive trusts the trust extends past two domains in a set tree. In this case, two entities can access the other’s domains and trees.
In one way transitive trusts, a user is given access to another domain or tree; however, the other domain cannot permit access to further domains. This permission set is similar to the classic administrator and end-user case. In this case, the admin can see most trees in the forest to include an end-user’s domain. The end user; however, cannot access other trees beyond his or her own domain.
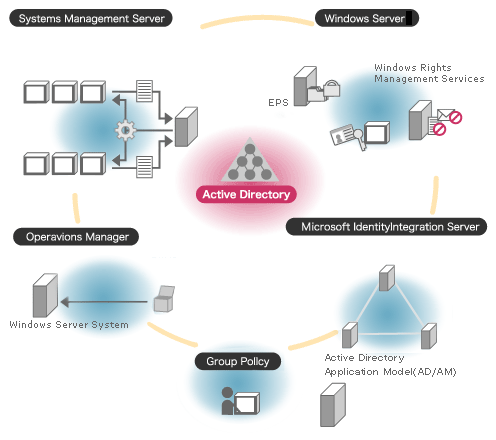
Active Directories are primarily used to organized large organizations or corporations computer networks and data. They help save significant time and cost by eliminating the need to visit each computer individually to perform routine maintenance and upgrades. Although the learning curve to operating an Active Directory is significant, when operated properly they can result in more efficient large network operation.
How Does an Active Directory Work?
An Active Directory acts as a special-purpose database for Windows computers. The system is not designed as a Windows registry replacement, rather, it is designed to manage large numbers of read and search operations as well as changes and updates. The data stored in Active Directory is designed to be replicated, hierarchical, and extensible. Since the data gets replicated, it is not considered as useful for dynamic information like CPU performance statistics. Relevant information that is normally stored in AD includes user contact data, printer queue information, and specific computer or network configuration data. The information stored in AD is in Object and attribute format defined in the AD schema.
What Are Active Directory Partitions?
Active Directory has three primary partitions or naming contexts. These include: schema, domain, and configuration. The domain partition consists of object types such as contacts, users, groups, computers, and organizational units. The Schema partitions consists of class and attribute definitions, while the configuration partition contains service configuration data, partitions, and websites. Active Directory information can be viewed at one of three levels including: forests, trees, or domains. The forest view includes all objects in the directory, tree structures will hold one or more domains, and the lowest-level views are for single domains. For example, in a large company or organization there will be dozens to hundreds of users and processes. The forest view will consist of the entire network of users and computers at a specific location. Within the forest will be trees that hold information on program data, domain controllers, and other relevant information. Each of these trees will then contain data on specific objects to include individual domains which can be controlled and categorized.
Active Directory Objects
Active Directory structures are grouped into two basic or broad categories: resources and security principals. Resources are typically printer or networked hardware resources while security principals relate to computer accounts or groups and are assigned unique security identifiers (SIDs). Every object in AD represents a single entity and the associated attributes. Objects are able to have other object types as attributes and are uniquely identified by their name and attributes. The definition for an object is made by its schema. An attribute object is used to define multiple schema objects which contain information regarding the extensibility of the data set. Since Schema object changes automatically propagate throughout the system, making changes or deactivating objects is a deliberate process to avoid unintended consequences. Once an object is created, it cannot be deleted just deactivated.
What Are Active Directory Organizational Units?
Domain objects with AD can be grouped into Organizational Units (OUs). An OU can be used to provide a hierarchy grouping for a domain. This act simplifies the administration of the domain and can be tailored to resemble the organizational structure in either managerial or geographic terms. OUs can be designed to contain other OUs to act as a container. Microsoft recommends that AD users make use of an OU for structure vice a domain in order to make the implementation of policies and administration easier. The OU level is also where group policies that are AD objects (Group Policy Objects) are normally applied. Delegation of administrator privileges also occur at this level but can be accomplished using attributes or individual objects.
How Does Active Directory Handle Duplicate Usernames?
Active Directory does not allow duplicate usernames to be entered. One of the common work-arounds for this is to add a numeric digit to the end of the person’s username. Alternatively, a separate ID system can be implemented at the administrator level to use as an account name in place of the specific user name. The importance of making the decision on how to handle unique user names in AD increases with the size of an organization. This is due to the fact of the odds of having multiple students with identical names increasing with the size of the group being managed.
How Are Shadow Groups Managed?
In AD, organization units are not able to be assigned as owners or trustees. Members of OUs cannot be assigned rights to directory objects with only groups being selectable. Since OUs don’t provide access permissions and objects within an OU don’t inherit privileges from the container, it is considered a design limitation of Active Directory. The most common work-around for AD administrators is to write a script to automatically create and maintain a user group for each OU in the directory. These scripts are written in PowerShell or Visual Basic and run at pre-determined timeframes to match the OU account membership. They cannot instantly update the security groups, which are referred to as “Shadow Groups” within AD and is a known limitation of the system.
How Does Replication Work in Active Directory?
Active Directory makes use of a ‘pull’ system to receive changes from the server. The Microsoft Knowledge Consistency Checker (KCC) makes a replication topology of site links that uses defined sites to manage traffic. Intrasite replication occurs automatically once a change notification is received. This action triggers peers to start replication cycles. Intersite replication occurs less frequently under AD and do not use change notification by default, but can be modified by the administrator to do so.
Active Directory makes use of Remote Procedure Calls (RPC) using the Internet Protocol (IP) (RPC/IP). SMTP can be used for cross-site replication; however, only for changing the Schema, Configuration, or Partial Attribute Set NCs. The SMTP replication option cannot be used for the default Domain partition. The programming interface for AD is available through the Microsoft COM interface provided by the Active Directory Service Interface.
Active Directory Database
At the time of this writing, the Active Directory database in Windows 2000 Server uses the Jet Blue-based Extensible Storage Engine. This engine is currently limited to 16 terabytes and two billion objects. Out of these two billion, the number of security principals is limited to one billion under each domain controller’s database. Under Windows Server 2003 a third main table was added to the Microsoft NTDS database (data and link table) to store security descriptor single instancing.
Active Directory Lightweight Directory Service
The Active Directory Lightweight Directory Service (AD LDS) is Microsoft’s light-weight implementation of Active Directory. The service was formerly known as Active Directory Application Mode (ADAM) and can be run on any computer running Microsoft Windows Server. Providing similar functionality as AD, the lightweight implementation does not require the administrator create domains or domain controllers. It does provide a Data Store to place directory data and a Directory Service with a LDAP interface. One server can run multiple instances of AD LDS.
Active Directory UNIX Interoperability
UNIX or UNIX-like operating systems can interoperate at some level through the use of LDAP clients. A number of Windows specific component attributes cannot be interpreted by non-Windows computers such as support for one-way trusts or Group Policies. Active Directory integration is offered by third-parties for UNIX platforms such as Linux, Mac OS X, and a number Java based applications.
What Are Some Open Source Active Directory Alternatives?
Directory services were not created with the release of Microsoft Active Directory. Originally, they were part of an Open Systems Interconnection (OSI) initiative to get industry to agree to common network standards. These standards encourage cross-vendor interoperability and X.500 was the first set of standards developed by ITU and ISO in the mid-1980’s. From this work evolved the LDAP (Lightweight Directory Access Protocol) that is used to support communication and look-ups using the TCP/IP stack and is common across all major implementations of directory services in use today. Two of the popular open source alternatives to Microsoft’s Active Directory include the Fedora Directory Server, the Apache Directory Server, and freeIPA.
Fedora Directory Server
The Fedora Directory Server is released as open source and functions as a LDAP server. Fedora is known for reliability and high performance and lets administrators manage users and groups. The server runs on the Linux operating system and can serve as the database for email services, remote authentication, and other centrally managed server applications. Fedora also includes a phonebook, organization charge, and allows users to manage personal data if setup by the administrator. The Fedora organization view is grouped in structure similar to a tree and is able to synchronize with Microsoft Active Directories. The server also supports Multi-Master Replication and is now scalable to tens of thousands of concurrent users with hundreds of gigabytes of information. The current release contains support for LDAPv3, Active Directory user and group synchronization, SSL v3, TLSv1, and SASL. The current installation also includes a graphical console for user, group, and server management.
Apache Directory Server
The Apache Directory Server is another open source LDAP directory that is implemented in the Java programming language. Apache provides a back-end database to manage network resources and users and is designed to allow components to be installed on the server. Some examples of Apache component installations include DHCP and DNS. The primary communications that occur with the Apache Directory Server use the JNDI (Java Naming and Directory Interface). The implementation is now Schema aware and can perform all LDAP related operations and supports DSML/LDIF format support if required to communicate with the Active Directory.
freeIPA
freeIPA is another open source server package that has been under development since prior to 2008 and combines Fedora, the 389 Directory Server, MIT Kerberos, NTP, Dogtag Certificate System, and NTP. The software deploys with both web interface and command-line administration tools. In the latest release of the software package DNS and the Dogtag Certificate Server were added to the project and support for host identities, netgroups, and automount per location were added to an enhanced administrative framework.

Jaspreet
Well Explained
Vimal
Hi, thank you very much,Explained very well..
I found this video very useful too..Have a look..very simple yet knowledgeable..
http://www.youtube.com/watch?v=1YUEIlrm6a0&feature=relmfu
anil
Thank You Very Much….
It’s a very nice explanation of AD.
Vivin
Excellent explanation.Helped me understand the basics very well
ricky
NICE INFO.
GOOD INSIGHT OF AD
Sandeep kumar
Oh!!
this is realy too good explanation of AD.
I like..
Thanks
Jabasingh
Very informative, thanks a lot…It would be more effective if you also provide the steps to install AD in a system…
monish
It gave me a good idea about “ACTIVE DIRECTORY”… Thanks alot…
Srinivas
excellent, i never find this type of material…………….
Arun
Thanks for giving a lot information about AD but it seems we need to get a deeper part of Directory so that it will be helping us in knowing the things better.
Thanks
Arun Chindra
Ramadas
what is the difference between active directory and domain
Skumar
good technique of explaination
panday
why we use active directory please explain
sanjay Badola
dear sir kindly conform me what is diffrent server 2008 and server 2008 r2 ?
Sushil Ror
Thanku very much
shital
THANKS
prasad
what is defernce doman controler member server
prasad
what is active directory
Hafsat Albasu
An active directory is a directory structure used on Microsoft Windows computers and servers to store information about networks and domains
Gerry
Thanks for the simple description of AD. My own organisation is currently introducing it and, as a semi-techie, I was looking for a simple description of what it is. Your article fit the bill perfectly.
ashish
i believed that wikipedia is the best source in the world but after visting tech-site i found my self wrong.this tech site gives so simple answers that i cant explain.
thanks to you tech.
ashish
rohit
your information is best and useful for me….
Dharma
thnx for the information
Marlon Franco
you’re welcome Dharma
mohammed jabbar
Please any one know AD tools to to query the Emails and contact lsit
jayant
can we restore 2k3 ad backup on 2k8 server?
Ben
Don’t forget to audit Active Directory changes!
sharma
pl tell me that how to install Exchange servver 2010 in server 2008 R2 some problem to install exchange server 2010
deepak reddy
you have asked something which is not possible to explain in few steps..
primarily..you just cant install exchange server 2010 in your server 2008 like your xp..you need to consider many things before going ahead.
1.you must have active directory installed and configured properly
2.primary and secondary dns configured correctly
3.if your organization is going offline for some maintenance you must configure vpn’s of course you must need vpns while going online also..
4.if you are migrating from 2003 server to 2008 server active directory’s must be cascaded …really painfull job
though you can install exchange without all these you will get a glimpse of exchange server…
deepak reddy
you have asked something which is not possible to explain in few steps..
primarily..you just cant install exchange server 2010 in your server 2008 like your xp..you need to consider many things before going ahead.
1.you must have active directory installed and configured properly
2.primary and secondary dns configured correctly
3.if your organization is going offline for some maintenance you must configure vpn’s of course you must need vpns while going online also..
4.if you are migrating from 2003 server to 2008 server active directory’s must be cascaded …really painfull job
though you can install exchange without all these you will get a glimpse of exchange server…
Akhtar Mallick
u gave me a good knowledge thnx………………………….
Nishikant Bhole
It is very useful and funtastis information
thank you @ nr bhole
kris.biswas
This is a very useful knowledge for the beginners..
Ranjitha
Very good explanation. It is more clear for beginners.
saurav ghosh
good stuff about AD.
Dev Narayan Panday
quit Knowledgeable for beginners
ISHITA
not at all helpful
Vijaya Ram
Hi Ishitha,
Can you tell me why it is not at all usefull?
Please let us know if you have useful explaination on ADS.
Warm Regards,
Vijaya Ram
NMK
Pls tell me why it is not usefull and give a reply with usefull msg…
DURGARAO
IT IS WONDER FULL WEBSITE TO KNOW ABOUT THE ADS[ACTIVE DIRECTORY SERVICES]
Srinivas
Its fine and understandable……………………gud