A botnet or robot network is a group of computers running a computer application that only the owner or software source controls and manipulates. The botnet may refer to a legitimate network of several computers that share program processing amongst them.
Usually though, when people talk about botnets, they are talking about a group of computers infected with a malicious kind of robot software, the bots, which present a security threat to the computer owner. Once the robot software (also known as malicious software or malware) has been successfully installed in a computer, the computer becomes a zombie or a drone, unable to resist the bot commander’s commands.
A botnet may be small or large depending on the complexity and sophistication of the bots used. A large botnet may be composed of ten thousand individual zombies. A small botnet, on the other hand, may be composed of only a thousand drones. Usually, the zombie computers’ owners do not know that an individual or a group of malware runners are remotely controlling and exploiting their computers through Internet Relay Chat (IRC).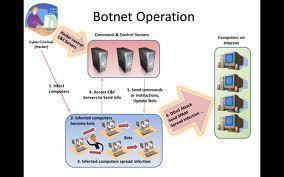
There are various types of malicious bots that have already infected and are continuing to infect the Internet. Some bots have their own spreaders – the script that lets them infect other computers (this is the reason some people dub botnets as computer viruses) – while some smaller types of bots do not have such capabilities.
Different Types of Bots
Here is a list of the most used bots on the Internet today, their features, and command set.
XtremBot, Agobot, Forbot, Phatbot
These are currently the best known bots with more than 500 versions on the Internet today. The bot is written with C++ with cross platform capabilities as a compiler and GPL as the source code. These bots can range from the fairly simple to highly abstract module-based designs. Because of its modular approach, adding commands or scanners to increase its efficiency in taking advantage of vulnerabilities is fairly easy. It can use libpcap packet sniffing library, NTFS ADS, and PCRE. Agobot is quite distinct in that it is the only bot that uses other control protocols besides IRC.
UrXBot, SDBot, UrBot, and RBot
Like the previous bot types, these bots are published under GPL. Unlike the above mentioned bots, these bots are less abstract in design and written in rudimentary C compiler language. Although its implementation is less varied and its design less sophisticated, these type of bots are well known and widely used on the Internet.
GT-Bots and mIRC based bots
These bots have many versions on the Internet mainly because mIRC is one of the most used IRC client for Windows. GT (global threat) is the common name for bots scripted with mIRC. GT-bots use the mIRC chat client to launch a set of binaries (mainly DLLs) and scripts. Their scripts often have the file extensions .mrc.
Malicious Uses of Botnets
A botnet has many malicious applications. Among the most popular botnet uses are the following:
Denial of Service Attacks
A botnet can be used as a distributed denial of service weapon. It attacks a network or a computer system in order to disrupt service through the loss of connectivity, consumption of the victim network’s bandwidth, and overloading the victim’s computer system’s resources. Botnet attacks are also used to damage or take down a competitor’s website.
Botnets can target any Internet service. This can be done through flooding the website with recursive HTTP or bulletin board search queries. This mode of attack in which higher level protocols are utilized to increase the effects of an attack is termed spidering.
Spamming and Traffic Monitoring
A botnet can also be used to take advantage of an infected computer’s TCP/IP’s SOCKS proxy protocol for networking applications. After compromising a computer, the botnet commander can use the infected unit (a zombie) in conjunction with other zombies in his/her botnet (robot network) to harvest email addresses or to send massive amounts of spam or phishing mails.
Moreover, a bot can also function as a packet sniffer to find and intercept sensitive data passing through an infected machine. Typical data that these bots look out for are usernames and passwords that the botnet commander can use for his/her personal gain. Data about a competitor botnet installed in the same unit is also mined so the botnet commander can hijack this other botnet.
Keylogging and Mass Identity Theft
An encryption software within the victims’ units can deter most bots from harvesting any real information. Unfortunately, some bots have adapted to this by installing a keylogger program in the infected machines. With a keylogger program, the bot owner can use a filtering program to gather only the key sequence typed before or after interesting keywords like PayPal or Yahoo mail. This is one of the reasons behind the massive PayPal account thefts for the past several years.
Bots can also be used as agents for mass identity theft. It does this through phishing or pretending to be a legitimate company in order to convince the user to submit personal information and passwords. A link in these phishing mails can also lead fake PayPal, eBay, or other websites to trick the user into typing in the username and password.
Botnet Spread
Botnets can also spread other botnets in the network. They do this by convincing the user to download them, after which the program is executed through FTP, HTTP, or email.
Pay-Per-Click Systems Abuse
Botnets can be used for financial gain by automating clicks on a pay-per-click system. Compromised units can be used to click automatically on a site upon browser activation. For this reason, botnets are also used to earn money from Google’s Adsense and other affiliate programs by using zombies to artificially increase an advertisement’s click count.



Frankln
How can i use botnet software to decode a network time code?
roselin
explanations about…how to detect the botmaster a d the software used for it