IPSec Policies
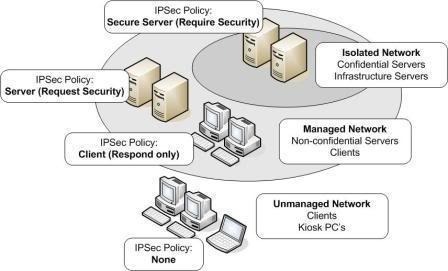
IPSec Policies Overview IPSec encrypts data information contained in IP datagrams through encapsulation to provide data integrity, data confidentiality, data origin authentication, and replay protection. The two main IPSec components that are installed when you install IPSec are the IPSec Policy Agent and the IPSec driver. The IPSec Policy Agent is a service running on …