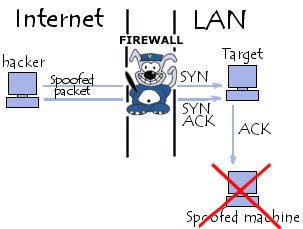
IP Address Spoofing
IP address spoofing denotes the action of generating IP packets with fake source IP addresses in order to impersonate other systems or to protect the identity of the sender. Spoofing can also refer to forging or using fake headers on emails or netnews to – again – protect the identity of the sender and to …