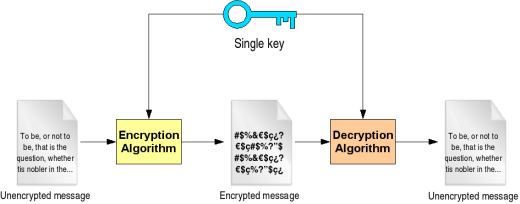
ATM Skimmer
An ATM skimmer is a card reader that is installed on some ATMs by criminals in order to steal the card numbers and PINs of the victims who use them. ATM skimmers vary in sophistication, but may be installed either directly within an ATM or next to it and may either interfere with the ATM’s …