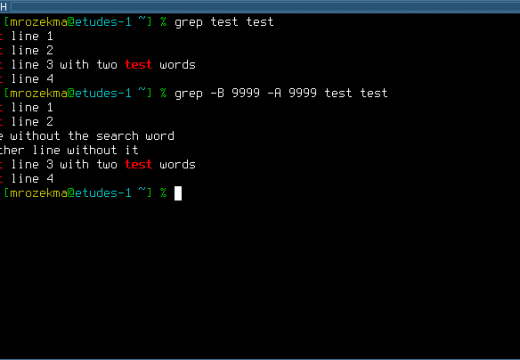
The History of UNIX
UNIX is one of the most important operating systems ever developed. What made Unix stand out in the crowd of countless other operating systems is that it was a competent operating system that was extremely affordable and worked on low cost hardware. Economics definitely played a large part in UNIX’s popularity and today it is …