IPSec Review
IPSec is a framework of open standards for encrypting TCP/IP traffic within networking environments. IPSec works by encrypting the information contained in IP datagrams through encapsulating to provide data integrity, data confidentiality, data origin authentication, and replay protection.
IPSec uses cryptography to provide authentication, data integrity, and data confidentiality services. Authentication deals with verifying the identity of the computer sending the data, or the identity of the computer receiving the data. IPSec can use digital certificates, the Kerberos v5 authentication protocol, or pre-shared keys as an authentication method. Anti-replay ensures that the authentication data cannot be interpreted as it is sent over the network. IPSec can provide non-repudiation. With non-repudiation, the sender of the data cannot at a later stage deny actually sending the data. Data integrity deals with ensuring that the data received at the recipient has not been tampered with. A hashing algorithm is used to ensure that the data is not modified as it is passed over the network. The hashing algorithms which can be used by IPSec are Message Digest (MD5) ad Secure Hash Algorithm 1 (SHA1). Data confidentiality ensures that data is kept private by applying encryption algorithms to data before it is sent over the network. IPSec uses encryption algorithms such as Data Encryption Standard (DES), Triple DEC (3DES), or 40-bit DES to provide data confidentiality.
IPSec uses the Authentication Header (AH) protocol and Encapsulating Security Payload (ESP) protocol to provide data security on client computers, domain servers, corporate workgroups, LANs, WANs and remote offices. The Authentication Header (AH) protocol provides data authentication and integrity, and can therefore be used on its own when data integrity and authentication are important to the organization but confidentiality is not. The AH protocol does not provide for encryption, and therefore cannot provide data confidentiality. The Encapsulating Security Payload (ESP) protocol ensures data confidentiality through encryption, data integrity, data authentication, and other features that support optional anti-replay services. To ensure data confidentiality, a number of encryption algorithms are used. The main difference between the AH protocol and the ESP protocol is that the ESP protocol provides all the security services provided by the AH protocol, together with data confidentiality through encryption.
When you install IPSec, the two main IPSec components which are installed are the IPSec Policy Agent and the IPSec driver. The IPSec Policy Agent is a service running on a Windows Server 2003 computer that accesses IPSec policy information. The IPSec Policy Agent accesses the IPSec policy information in the local Windows registry or in Active Directory. The IPSec Policy Agent then passes information to the IPSec driver. The IPSec driver performs a number of operations to enable secure network communications such as initiating IKE communication, creating IPSec packets, encrypts data, and calculates hashes.
IPSec can operate in either Tunnel mode or in Transport mode. IPSec Tunnel mode should be used to provide security for WAN and VPN connections that use the Internet. In tunnel mode, IPSec encrypts the IP header and the IP payload. With tunneling, the data contained in a packet is encapsulated inside an additional packet. The new packet is then sent over the network. In Transport Mode, the default mode of operation used by IPSec, only the IP payload is encrypted. Transport mode is used for end-to-end communication security between two computers on the network.
IPSec policies are used to apply security in your network. The IPSec policies define when and how data should be secured. The IPSec policies also determine which security methods to use when securing data at the different levels inyour network. You can configure IPSec policies so that different types of traffic are affected by each individual policy. IPSec policies can be applied at the Active Directory domain level, site level, OU level, and it can be applied on computers and applications. You can use a security method to define how an IPSec policy should deal with traffic matching an IP filter.A filter action can be used to define how the IPSec driver should secure traffic. The filter actions result in either of the following events: Drops traffic, Allows Traffic, or Negotiates security. IPSec filters can be used to filter out unauthorized traffic. Through security filters, you can filter traffic according to the following: Traffic allowed, Traffic to secure, or Traffic to block. You can also group multiple security filters into a filter list.
IPSec Management Tools
The IP Security Policy Management snap-in is used to manage IPSec, create IPSec policies and edit existing IPSec policies, and assign IPSec policies. You can also use the IP Security Policy Management tool to add and remove filters which are applied to IPSec policies. To work with the IP Security Policy Management snap-in, you first have to create a MMC console for the snap-in.
When you install the IPSec snap-in, you need to select which IPSec policy you want to manage, and on what network level you want to manage IPSec. You can select either of the following options:
- Manage a local IPSec policy on the computer.
- Manage the local IPSec policy a different computer.
- Manage the default policy for the domain in which the computer resides.
- Manage the default policy for a different domain.
You can also configure IPSec using the Netsh command-line utility. The netsh command-line utility replaces the previously used Ipsecpol.exe command-line utility. The netsh command-line utility cannot though be used to manage IPSec on Windows XP machines.
The Netsh command-line utility can be used to manage the following aspects of IPSec:
- View information on IPSec policies.
- Configure startup security for computers.
- Configure default traffic exemptions.
- Enable IPSec driver event logging.
- Troubleshoot IPSec configuration.
Windows Server 2003 includes the new IP Security Monitor tool which is implemented as an MMC snap-in. The IP Security Monitor tool provides enhanced IPSec security monitoring.
With the IP Security Monitor tool, you can perform the following administrative activities:
- Customize the IP Security Monitor display.
- Monitor IPSec information on the local computer.
- Monitor IPSec information on remote computers.
- View IPSec statistics.
- View information on IPSec policies.
- View security associations information.
- View generic filters.
- View specific filters.
- Search for specific filters based on IP address.
IPSec supports the new Resultant Set of Policy (RSoP) feature of Windows Server 2003. The Resultant Set of Policies (RSoP) calculator can be used to determine the policies which have been applied to a particular user or computer. Resultant Set of Policy (RSoP) sums all group policies which are applied to a user and computer in a domain. This includes all filters and exceptions. You can use the feature through the Resultant Set Of Policy (RSoP) Wizard or from the command-line to view the IPSec policy that is applied.
How to create an MMC console for the IP Security IP Security Policy Management snap-in
- Click Start, click Run, type mmc in the Run dialog box, and then click OK.
- Click the File Menu item, and select Add/Remove Snap-in.
- The Add/Remove Snap-in dialog box opens. Click Add.
- The Add Standalone Snap-In dialog box opens.
- In the Available Standalone Snap-ins list select IP Security Policy Management, and then click Add.
- The Select Computer Or Domain dialog box opens.
- Click the Local Computer option.
- Click Finish.
- Click Close to close the Add Standalone Snap-in dialog box.
- Click OK to close the Add/Remove Snap-in dialog box.
How to enable IPSec for an Active Directory domain
- Click Start, click Run, type mmc in the Run dialog box, and then click OK.
- Click the File Menu item, and select Add/Remove Snap-in.
- The Add/Remove Snap-in dialog box opens. Click Add.
- The Add Standalone Snap-In dialog box opens.
- Select Group Policy Object Editor, and then click Add.
- The Select Group Policy Object dialog box opens. Click Browse.
- The Browse For A Group Policy Object dialog box opens.
- Select Default Domain Policy, and then click OK.
- Click Finish.
- Click Close to close the Add Standalone Snap-in dialog box.
- Click OK to close the Add/Remove Snap-in dialog box.
- Expand Domain Policy, expand Computer Configuration, expand Windows Settings, expand Security Settings, expand IP Security Policies on Active Directory.
- Select IP Security Policies On Active Directory.
- The details pane displays all available IPSec policies.
- Right-click the IPSec policy which you want to assign, and then click Assign from the shortcut menu.
How to use the netsh command-line utility to manage IPSec
Before you can use the netsh command-line utility to manage IPSec, you first have to change the utility to the ipsec context.
The two types of command modes which you can utilize for IPSec makes different IPSec functions available:
- netsh ipsec static mode commands; used to carry out the same management tasks as is available in the IP Security Policy Management. You can create IPSec policies and edit existing IPSec policies, and assign IPSec policies. The current IPSec policy configuration remains unchanged.
- netsh IPSec dynamic mode commands; used to view the existing IPSec state. The current IPSec policy configuration is affected by the netsh IPSec dynamic mode commands.
To change the netsh command-line utility to the ipsec context,
- Click Start, click Run, type cmd, and then click OK.
- When the command prompt window, enter netsh ipsec.
A few typically used netsh commands and switches are:
- netsh ipsec static add policy name; used to create an IPSec policy.
- netsh ipsec static delete all; used to delete all existing IPSec policies, filter actions, and filter lists.
- netsh ipsec dynamic set policy name; used to configure an IPSec policy name.
- netsh ipsec dynamic delete policy name; used to delete an IPSec policy name.
- netsh ipsec dynamic export policy name; used to export all IPSec policies to file.
Confiuring IPSec
You configure IPSec through configuring the following aspects of IPSec policies:
- Assign the predefined default IPSec policies.
- Creating customized IPSec policies that includes customized rules and filters.
- Control how IPSec policies are applied.
- Apply IPSec policies at different levels on the network.
You can use either of these methods to configure IPSec policies:
- You can use the IP Security Policy Management snap-in to configure IP security policies on the local computer. To create a new IPSec policy, you have to right-click the IP Security Policies node in the IP Security Policy Management snap-in, and then click Create IP Security Policy.
- You can use the Group Policy Object Editor snap-in to change local and domain GPOs. To create a new IPSec policy, you have to right-click the IP Security Policies node in the Group Policy Object Editor and then click Create IP SecurityPolicy.
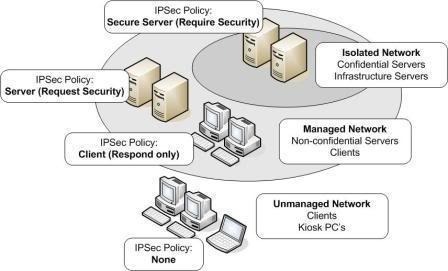
When you open the Security Policy Management snap-in, the following predefined default IPSec policies are displayed:
- Client (Respond Only): The Client (Respond Only) default IPSec policy has the following characteristics:
- Least secure default policy.
- The computer assigned the policy never initiates secure data communication.
- The computer only responds to IPSec requests from other computers who request it.
- Contains the default response rule that creates dynamic IPSec filters for inbound and outbound traffic based on the protocol and port which was requested.
- The predefined policy settings for the Client (Respond Only) default IPSec policy are listed here:
- IP Filter List; All
- Filter Action; None
- Authentication; Kerberos
- Tunnel Setting; None
- Connection Type; All
- Secure Server (Request Security): The Secure Server (Request Security) default IPSec policy has the following characteristics:
- The computer prefers and initiates secure data communication.
- If the other computer supports IPSec, secure data communication will take place.
- If the other computer does not support IPSec, the computer will allow unsecured communication with that computer.
- Contains three rules, and predefined policy settings:
- The predefined policy settings for Rule 1 are:
- IP Filter List; All IP Traffic
- Filter Action; Request Security (Optional)
- Authentication; Kerberos
- Tunnel Setting; None
- Connection Type; All
- The predefined policy settings for Rule 2 are:
- IP Filter List; All ICMP Traffic
- Filter Action; Permit
- Authentication; N/a
- Tunnel Setting; None
- Connection Type; All
- The predefined policy settings for Rule 3 are:
- IP Filter List; Dynamic
- Filter Action; Default Response
- Authentication; Kerberos
- Tunnel Setting; None
- Connection Type; All
- Secure Server (Require Security): The Secure Server (Require Security) default IPSec policy has the following characteristics:
- Only secure data communication is allowed.
- If the other computer does not support IPSec, the connection is not established.
- Contains three rules, and predefined policy settings:
- The predefined policy settings for Rule 1 are:
- IP Filter List; All IP Traffic
- Filter Action; Require Security
- Authentication; N/a
- Tunnel Setting; None
- Connection Type; All
- The predefined policy settings for Rule 2 are:
- IP Filter List; All ICMP Traffic
- Filter Action; Permit
- Authentication; Kerberos
- Tunnel Setting; None
- Connection Type; All
- The predefined policy settings for Rule 3 are:
- IP Filter List; Dynamic
- Filter Action; Default Response
- Authentication; Kerberos
- Tunnel Setting; None
- Connection Type; All
You can also create customized IPSec policies that include customized rules and filters that suit specific security requirements of the organization. Customized IPSec policies can be created in the IP Security Policy Management MMC. You can also create your own IPSec policy by using the IP Security Wizard which you can initiate from within the IP Security Policy Management MMC.
After you have followed the prompts of the IP Security Policy Wizard to create a create your own IPSec policy, you can access the properties of the IPSec policy to add, remove, and configure rules, filters, filter lists, and security actions for the policy.
The Properties dialog box of an IPSec policy contains the following tabs:
- General tab; used to configure general type configuration settings for he IPSec policy, including the following:
- Configure the policy name in the Name text box.
- Specify a description for the policy in the Description text box.
- Specify the interval for which clients using this specific policy checks for policy updates in the Check For Policy Changes Every box.
- Set the key exchange settings for the policy by clicking the Settings button. The Key Exchange Settings dialog box is displayed once you click the Settings button. On the Exchange Settings dialog box you can specify when new keys are generated for the policy.
- Rules tab; used to configure the rules for the IPSec policy, including the following:
- Configure properties for rules.
- Activate or deactivate rules for the policy
- Change the list of rules using the Add, Edit and Remove buttons.
- Set whether the Security Rule Wizard is initiated and used to add a new rule by selecting/deselecting the Use Add Wizard checkbox.
If you have deselected the Use Add Wizard checkbox on the Rules tab of the Properties dialog box of an IPSec policy, and you click the Edit button on the Rules tab, then the Edit Rule Properties dialog box opens.
The Edit Rule Properties dialog box contains the following tabs which you can use to set configuration settings:
- IP Filter List tab; used to add, remove, and configure the filter lists for the rule. All currently configured filter lists are displayed in the IP Filter Lists list.
- Filter Action tab; used to configure filter actions for the rule. The current filter actions defined for the rule are listed in the Filter Actions list. The Edit, Add, and Remove buttons can be used to change, add and remove filter actions for the rule. You can also specify whether the IP Security Filter Action Wizard should be initiated when a new filter action is added by enabling the Use Add Wizard checkbox.
- Authentication Methods tab; used to set the authentication method(s) which should be used for the rule. Options include Kerberos, digital certificates, or pre-shared keys. If you define more than one authentication method, you can set the order of precedence for the authentication methods.
- Tunnel Setting tab; used to configure whether the rule should establish an IPSec tunnel with another end system.
- Connection Type tab; used to set the connection type for the rule:
- All Network Connections option.
- Local Area Network option.
- Remote Access option.
How to create a customized IPSec policy:
- Open the IP Security Policy Management console.
- Select IP Security Policies.
- Right-click the security policy which you want to customize and then click Properties from the shortcut menu.
- When the Properties dialog box of the security policy opens, click the Rules tab.
- Find the rule which you want to change, and then click the Edit button.
- Click the Filter Action tab.
- Proceed to customize the filter action.
- Click the Security Methods tab.
- If you want to create a new security method, click Add.
- If you want to remove an existing security method, click Remove.
- If you want to change an existing security method, click Edit.
- To add a security method, click Custom, and then click Settings.
- The Custom Security Method Settings dialog box opens.
- To provide data integrity for the IP header and payload, enable the Data and address integrity without encryption (AH) checkbox. Select either the MD5 option or the SHA1 option as the Integrity algorithm.
- To provide data integrity and data confidentiality for the IP header and payload, enable the Data integrity and encryption (ESP) checkbox. Select either the MD5 option or the SHA1 option as the Integrity algorithm if you do not have the AH authentication protocol enabled. If you do have the authentication protocol enabled, click the None option. Select either the None option, DES option, or the 3DES option as the Encryption algorithm.
- To specify how many kilobytes of data must be transmitted before a new key is generated, click the Generate a new key every checkbox. Set a value that defines the number of kilobytes.
- To specify how many seconds must pass before a new key is generated, click the Generate a new key every option and enter a value which defines the number of seconds.
- Click OK.
How to create a new IPSec policy:
- Open the IP Security Policy Management console.
- Right-click IP Security Policies and then select Create IP Security Policy from the shortcut menu.
- The IP Security Policy Wizard initiates.
- Click Next on the IP Security Policy Wizard Welcome page.
- On the IP Security Policy Name page, provide a name and a description for the new IPSec policy, and then click Next.
- On the Requests for Secure Communication page, you can leave the Activate the default response rule option selected, or you can deselect the option. Click Next.
- On the Default Rule Authentication Method page, set the authentication method for the security rule, and then click Next.
- On the Completing the IP Security Policy Wizard page, select the Edit properties option, and then click Finish.
- The IP Security Policy Properties dialog box for the new policy opens so that you can change the properties of the policy, and change any security rules.
- Click Edit on the IP Security Policy Properties dialog box.
- The Edit Rule Properties dialog box opens. The tasks which you can perform are listed here:
-
- Add and remove security methods.
- Modify existing security methods.
- Set the order of precedence for security methods.
- Specify the utilization of session key perfect forward secrecy (PFS).
- Click the Authentication tab. The tasks which you can perform are listed here:
-
- Add and remove authentication methods.
- Set the order of precedence for authentication methods.
- Click OK to close the Edit Rule Properties dialog box.
- Before you assign the IPSec policy, first ensure that the IPSec service is running.
- In the IP Security Policy Management console, right-click the new policy name that you want to assign, and then click Assign from the shortcut menu.
Managing Filter Lists and Filter Actions
IP filters, IP filter lists, and filter actions and rules define the IP security policy. Filters define the source, destination and action for each specific rule.
When defining a filter action, you can choose between the following filter actions in the IP Security Policy Management MMC snap-in:
- Permit action (pass through action); used to allow traffic to pass through without applying any security rules and modifying the traffic. The traffic is simply allowed. Typically used for data that is considered non-sensitive.
- Block action; used to block all traffic.
- Allow Unsecured Communication With Non-IPSec Aware Computers; when used unsecured connections will be accepted by your computers. Generally recommended that you do not utilize this option.
- Accept Unsecured Communication, But Always Respond Using IPSec action; when used the computer will always request IPSec before allowing any connections, but it will allow unsecured connections. Secured connections will though always be requested. This option therefore allows for secured connections and unsecured connections.
- Use These Security Settings action; used to specify custom security methods which should be applied for connections matching the filter.
Before managing IPSec rules, consider the following factors:
- Address specific filters are supported.
- Protocol and port specific filters are supported.
- Inbound packets which do not match any filters are permitted.
- Outbound packets which do not match any filters are sent as unsecured packets.
- When filters are applied, they are applied in a definite sequence, starting from the most specific filter and moving to the least specific filter.
- The order in which filters appear in the IP Filter Lists list does not affect the order in which filters are applied.
- With an IKE security request, the source IP address of the request is used to search for a filter that matches.
- With an IKE security response, the actual response is affected by the security action specified and the tunnel setting.
You can manage filter lists and filter actions using either of these methods:
- Using the tabs available on the Edit Rule Properties dialog box.
- To access the Edit Rule Properties dialog box, open the IP Security Policy Management console, access the Properties dialog box of the particular IPSec policy, click the Rules tab and then click the Edit button.
- Using the Manage IP Filter Lists And Filter Actions dialog box.
- To access the Manage IP Filter Lists And Filter Actions dialog box, open the IP Security Policy Management console, right-click the IPSec policy that you want to manage, and then click Manage IP Filter Lists And Filter Actions from the shortcut menu.
The information that you need to provide when you add a new filter or change an existing filter are listed here:
- Source address and destination address to filter: You have to specify the source and destination address to be filtered using either of these methods:
- Protocols and ports to which the filter should apply: The protocols which you can specify include:
- EGP
- ICMP
- RAW
- RDP
- TCP
- UDP
To specify ports, you can use either of the following methods:
- Specify a single port.
- Specify a range of ports by using the From Any Port and To Any Port option.
Define whether the filter is a mirrored filter.
The IP Filter Properties dialog box can be used to modify a filter. When you click the Add or Edit buttons, the Properties dialog box of the specific filter opens, displaying the following tabs:
- Addresses tab: This where you configure the source and destination addresses which the filter should match.
Click the Source Address drop-down box to set the source address:
-
- My IP address, packets from this computer is secured.
- Any IP address; packets from any computer are secured.
- Specific DNS name; packets from the DNS name in Host name is secured.
- Specific IP address; packets from only the IP address which you specify is secured.
- Specific IP subnet; packets from the IP subnet which you specify is secured.
- DNS Servers dynamic; packets from the DNS server which the specific computer is using is secured.
- WINS Servers dynamic; packets from the WINS server which the specific computer is using is secured.
- DHCP Server dynamic; packets from the DHCP server which the specific computer is using is secured.
- Default Gateway dynamic; packets from the default gateway which the specific computer is using is secured.
- Click the Destination Address drop-down box to set the destination address.
To configure mirrored settings, selct or deselect the Mirrored checkbox:
-
If you only want to create one filter, you should deselect or uncheck the Mirrored checkbox.
-
If you want to create two filters using the same filter settings, click the Mirrored checkbox. A filter will be created to filter traffic to the specific destination, and another filter will be created to filter traffic from the specific destination.
-
If you want to create a filter for an IPSec tunnel, then you need to create two filter lists and ensure that the Mirrored checkbox is cleared or unchecked.
- Protocol tab: This is where you specify the protocols and ports to which the filter should apply. The protocols which you can specify include EGP, ICMP, RAW, RDP, TCP, or UDP. You can specify a single port, or you can alternatively specify a range of ports by using the From Any Port and To Any Port options.
- Description tab: You can provide a description for the filter in the Description tab.
How to modify an IP filter
- Open the IP Security Policy Management console.
- Double-click the IPSec policy that you want to configure.
- Click the Rules tab.
- Double-click the IPSec rule which holds the filter that you want to change.
- Click the IP Filter List tab.
- Click the Add button to configure an additional filter list.
- Click the Remove button to remove an existing filter list.
- Click an existing filter in IP Filter Lists list, and then click the Edit button to modify it.
- Click OK.
Assigning IPSec Policies in Group Policy
Before configuring IPSec policies for domains for Active Directory, consider the following factors:
- When you apply an IPSec policy to a Group Policy Object (GPO) in Active Directory, all computer accounts affected by the specific GPO will be assigned the IPSec policy.
- IPSec policies can be applied at the following levels within Active Directory:
- Domain
- Site
- Organizational unit (OU)
- You can only apply a single IPSec policy at a specific level in Active Directory.
- Organizational units (OUs) automatically inherit the IPSec policy of their associated parent OU in Active Directory.
- If you do not want a child OU to inherit the IPSec policy of its parent OU, you can use the block option to prevent it from being assigned to the child OU.
- An IPSec policy that is assigned for a domain in Active Directory has precedence over a locally applied IPSec policy.
- IPSec policy assigned for an organizational unit (OU) has precedence over domain level policies for members of the specific OU.
- An IPSec policy that is assigned to the lowest level organizational unit has precedence over an IPSec policy which is assigned to the higher level organizational units.
- The Windows Server 2003 Group Policy backup and restore tools do not include backing up and restoring IPSec policies. You have to use the Export Policies and Import Policies commands available on the Action menu of the IP Security Policy Management console.
- If you delete a GPO, the IPSec policy can still remain. You should therefore first unassign the IPSec policy prior to deleting the IPSec policy.
Best Practices for Implementing IPSec
A few recommendations for implementing IPSec, as defined by Microsoft, are listed here:
- Before you can implement any security measures and IPSec security policies to secure your network and mission critical data, you need to plan your IPSec implementation and configuration.
- You should develop a test tab and use the test lab to test the implementation of your IPSec policies before you implement any policies in your production network environment. Remember that some features of IPSec are not supported in all versions of the Windows operating systems. Windows Server 2003 does though support all the features of IPSec and it also includes IPSec-specific enhancements.
- Because pre-shared keys is considered the least secure supported authentication method, you should only use pre-shared keys when you cannot use the digital certificates or the Kerberos v5 authentication protocol. Pre-shared keys should really only be used in testing environments.
- You should refrain from using the Kerberos v5 authentication protocol for computers which are connected to the Internet. This is primarily because the identity of the computer remains unencrypted up to the point that the whole payload is encrypted.
- You should use digital certificates as the authentication method for computers which are connected to the Internet. When sending the certificate request, do not however transmit the name of the Certification Authority (CA) together with the request.
- For all computers which are connected to the Internet, only allow secured connections and communication to occur. You should ensure that the following options are disabled:
- Allow Unsecured Communication With Non-IPSec Aware Computers.
- Accept Unsecured Communication, But Always Respond Using IPSec.
- Diffie-Hellman key agreement enables two computers to create a shared private key that authenticates data and encrypts an IP datagram. IPSec in Windows Server 2003 includes support for the Group 3 2048-bit Diffie-Hellman key exchange which is much stronger and more complex than the previous Group 2 1024-bit Diffie-Hellman key exchange. If you need backward compatibility with Windows 2000 and Windows XP, then you have to use the Group 2 1024-bit Diffie-Hellman key exchange. You should though never use Group 1 768-bit Diffie-Hellman key exchange because it offers the lowest keying strength.
- If you are running Windows XP and Windows Server 2003 computers, use the Triple Data Encryption Standard (3DES) encryption algorithm which provides the strongest encryption algorithm. When you use 3DES, data is encrypted with one key, decrypted with another key, and encrypted again with a different key. If you running Windows 2000 computers, install the High Encryption Pack or Service Pack 2 so that 3DES can be used.
- The Windows Server 2003 IPSec Policy Management MMC snap-in should be used to manage IPSec policies. If you are planning a Windows Server 2003 IPSec implementation, then you have to use the Windows Server 2003 IPSec Policy Management MMC snap-in if you want to use the latest IPSec features.

Follow Us!