Rootkit
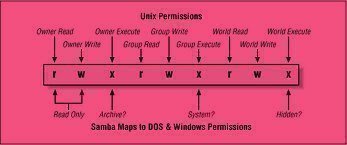
A rootkit is a type of computer malware that is created to hide programs or other computer processes from detection from both users and antivirus software programs. Once installed, a rootkit will typically obtain administrator or higher-level permissions on the infected computer. Although rootkits originated with the UNIX operating system by providing root access to …