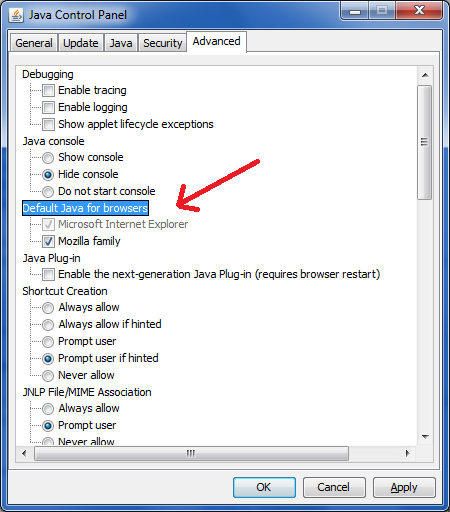
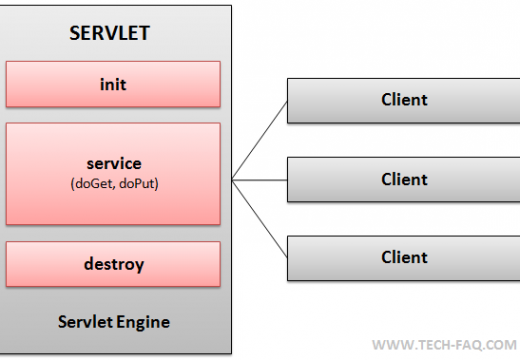
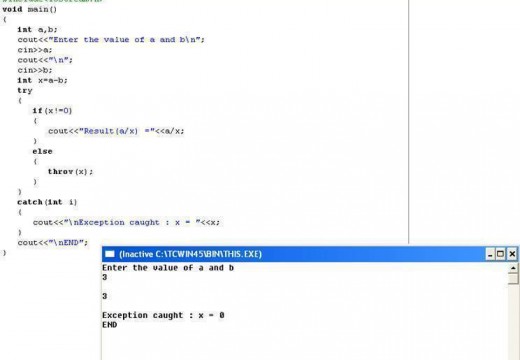
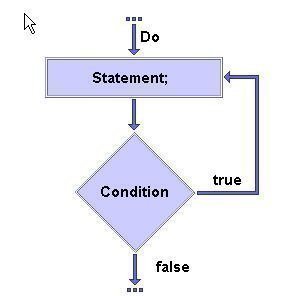
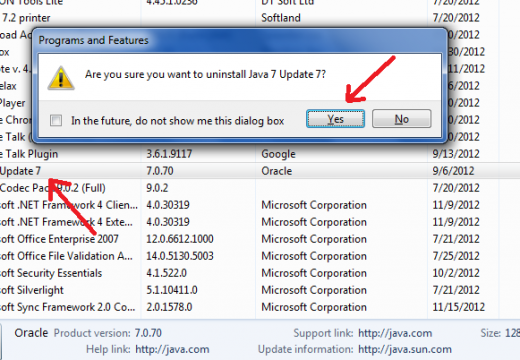
How to Enable Java
The Java Virtual Machine (JVM) is a collection of software programs and data modules that forms part of the Java and Java 2 platforms. JVM works across all platforms and it alters Java bytecode into machine understandable code and executes it. It acts as a clone of a Java processor allowing Java bytecode to be …