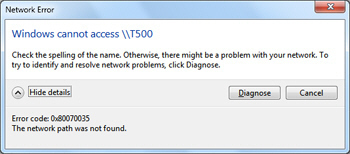
0x80070035
As the number of home computer users creating local networks increases, so does the number of Operating Systems (OS’s) used in homes or small business. As long as the version of Windows OS running on the network is Windows XP SP2 or newer, all of the computers should be able to be linked and information …