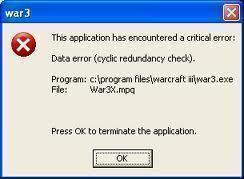
Data Error Cyclic Redundancy Check
The “Data Error Cyclic Redundancy Check (CRC)” is a problem with the mathematical process the computer does in order to ensure that data is properly transferred from a particular source to a specified destination. During the cyclic redundancy check, the computer determines if the data being transferred is not damaged. When users get a “Data …