Planning the Test Network Environment
Any successful network design deployment includes a testing strategy, and the execution of the testing plan. To test the network design, you have to plan the test network or environment, and then create the test network. A testing environment can contain one lab or multiple labs. You can build various labs to test specific components within the network design.
When planning your test environment, take time to create an environment that can prove whether or not the network design being tested is effective. You should create a test environment that will highlight issues or flaws within the network design.
There are a number of hardware components and devices that need to be included within the test network. A number of typical hardware components and devices that should exist within the test environment are listed here: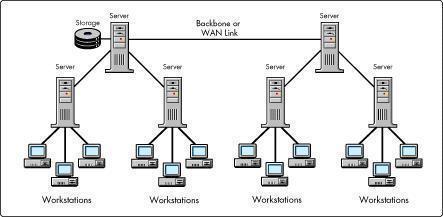
-
Network adapters
-
USB adapters
-
BIOS versions
-
Small Computer System Interface (SCSI) adapters
-
CD drives and DVD drives
-
Sound cards and video cards
-
Removable storage devices
-
Smart card readers
-
Keyboards
-
Mouse devices
For Windows Server 2003 test networks, you need to ensure that the configurations listed below exist in the test network.
-
Create and configure the different network technologies and network protocols in your test environment which you plan to implement for your network design.
-
Networking services: The networking services installed on your test servers should mirror those that you plan to deploy in the real on-line (production) environment. Configure the services as they would operate in the production environment, for instance, with regard to service startup types, and the actions which should occur when a service fails. Windows Server 2003 provides technologies and services that can be added to new networks and existing networks to meet the organization's business requirements. To use certain services, you many have to first implement specific technology or services on which these services depend. For instance, in order to use the Windows Server 2003 Active Directory directory service, you first have to install Transmission Control Protocol/Internet Protocol (TCP/IP) protocol, and the Domain Name System (DNS) service. Transmission Control Protocol/Internet Protocol (TCP/IP) is the primary protocol used in Windows 2000 and Windows Server 2003 networks, and many network services use the protocol. For this reason, TCP/IP is installed as part of the installation of Windows 2000 and Windows Server 2003. TCP/IP is a routable protocol. It is used by wide area networks (WANs) and the Internet. Another service other than the Active Directory directory service that is dependant on TCP/IP is the Internet Information Server (IIS) service.
The typical Windows services which you should include in your test environment are listed here, together with the main functions of each service:
-
Domain Name System (DNS) Server service: It is the DNS Server service that makes it possible for friendlier names to be used to locate and connect to hosts, and other network resources. DNS is used for name resolution, to provide a standard naming convention to locate IP hosts on the Internet. If you choose to fully integrate Active Directory and DNS, DNS information is stored directly in Active Directory. This means that a domain controller running the DNS Server service can be configured to deal with dynamic updates through Dynamic Host Configuration Protocol (DHCP), with Active Directory controlling access to DNS information.
-
Dynamic Host Configuration Protocol (DHCP) is used to manage IP addresses on a network using TCP/IP. To use DHCP, you first have to install the DHCP service on a computer, making it aDHCP server. DHCP can integrate with the DNS Server service, and the Active Directory directory service.
-
The Windows Internet Name Service (WINS) is used in Windows NT Server 4.0 and prior operating systems (OSs) for name resolution. WINS is typically used in routed networks for NetBIOS name resolution.
-
The Internet Information Services (IIS) version included in Windows Server 2003 is IIS 6.0. IIS is the most frequently used Web servers on the Internet and in intranets. If you are running a Windows Server 2003 Edition other than the Windows 2003 Server Web Edition, IIS has to be installed first in order to use its features and capabilities.
-
Windows Server 2003 includes the Terminal Services feature. When Terminal Services is configured in Remote Desktop For Administration mode (default), it can be used as a remote server management tool. The feature allows administrators to log on to a computer from a desktop and not the server console to perform administrative tasks. The components supported by the Windows Server 2003 Terminal Services service are Remote Desktop For Administration and Remote Assistance (RA).
-
The Microsoft Certificate Services can be installed to create and manage Certificate Authorities (CAs). CAs issues the digital certificates which are used in a PKI implementation to provide a number of features, including IPSec authentication, secure e-mail, secure communications between Web clients and servers, and local network and remote access logon authentication.
A service can be configured with one of the startup types listed below. The startup type controls when and how the service starts.
-
Automatic, the service starts automatically when the operating system starts or boots.
-
Manual, the service needs to be started manually by an Administrator. However, if a service or process needs to start a particular service, it can start the service.
-
Disabled, for a service with the Disabled startup type to start, the actual startup type needs to be changed to either Automatic or Manual. A service cannot start another service if that particular service's startup type is Disabled
You can configure the action that should occur when a service fails. The actions which you can configure are listed next:
-
Take No Action
-
Restart The Service
-
Run A Program
-
Restart The Computer
-
-
Domain structure: You should mirror the domain structure which you plan to implement in your production environment. You should include the configuration of following key components:
-
Domain trees: Here, you should configure how you are going to grouping one or multiple Windows Server 2003 domains in a tree. Domain trees are essentially a hierarchical arrangement of domains. Domain trees are created by adding child domains to a parent domain.
-
Forests: You should configure how one or multiple domain trees are going to be grouped into a forest.
-
Parent domains and child domains: You typically form domain trees by creating and adding one or multiple child domains to a parent domain.
-
Organizational units (OUs): You should reflect how objects are going to be stored into logical groups. OUs can be hierarchically arranged within a domain. An organization unit can contain objects such as user accounts, groups, computers, shared resources, and other OUs.
-
Sites: Define how the grouping of one or more Internet Protocol (IP) subnets which are connected by a reliable high-speed link are going to be done. Sites should be defined as locations that enable fast and cheap network access.
-
Trust Relationships: Tree-root trust and Parent-child trust is implicitly created by Active Directory when new domains are created. Shortcut trust, Realm trust, External trust and Forest trust differ to Tree-root and Parent-child trust, in that the former four trusts have to be explicitly created and managed. Because of the different types of trust relationships that can be created, you need to plan which type of trust relationship to create for the domains within your Active Directory environment.
-
-
Domain controllers: Create the necessary domain controllers within your test environment. The number of domain controllers which are needed within your domain are determined by the following factors:
-
The number of users in the domain.
-
The number of computers in the domain.
-
The application requirements in the domain. The level of fault tolerance required for the domain – at least two domain controllers should exist in the domain.
-
The different domain functions and roles affect performance and influence the number of domain controllers that should be deployed in the domain
-
-
Domain authentication method: You should install and configure the domain authentication which you plan to use in your production Active Directory environment, in your test network environment. Here, include the following as relevant to your network design:
-
Windows 2000 mixed domain functional level
-
Windows 2000 native domain functional level
-
Windows Server 2003 domain functional level
-
NT LAN Manager (NTLM) authentication protocol
-
Kerberos authentication protocol
-
-
Group Policy Object (GPO) settings: Group Policy settings are stored in a Group Policy Object (GPO). The types of Group Policy settings which can be stored in a GPO are computer configuration settings or user configuration settings. Creating a GPO is the initial step in ultimately applying Group Policy settings to user objects, and computer objects in Active Directory. When you create a new GPO, it is by default linked to the site, domain, or OU which was selected, when the GPO was created. The Group Policy settings stored in the GPO are applied to that particular site, domain or OU. You can though, at a later stage, link the GPO to other sites, domains, or OUs. You can use the Group Policy Management Console (GPMC) to determine which GPOs are enabled and being processed, and the manner in which GPOs are linked to sites, domains, and OUs. The GPMC can be used to examine all sites, domains, OUs and GPOs within your enterprise. It allows you to examine the settings of a specific GPO, and is can also be used to determine how your GPOs are linked to sites, domains, and OUs. The GPMC consists of an MMC, a set of automated scripts which can be run from the command line, and a set of batch files. The scripts included in the Group Policy Management Console (GPMC) can be used to list and view the following Group Policy Object (GPO) information:
-
Information on a specific GPO
-
All the GPOs in a domain
-
All disabled GPOs
-
View unlinked GPOs in a domain
-
View GPOs by policy extension
-
View GPOs by security group
-
View GPOs with duplicate names
-
View GPOs with no security filtering
-
View scope of management information
-
-
User accounts: These are Active Directory objects which uniquely identify network users. A user account enables a user to log on to the domain and to access resources. A local user account enables a user to log on to a computer and access local resources on that particular computer. A domain user account enables a user to log on to a domain, and access network resources. Built-in user accounts are typically used for administrative tasks. The security settings that you configure for a user, group, or computer determines and controls whether the particular security principal account has access to Active Directory, client computers, member servers, domain controllers, applications, and other network resources and services.
In your test network environment,
-
Assign permissions to security principal accounts so tat the users, group, or computers can access network resources.
-
Grant user rights to security principal accounts.
-
Creating a Testing Strategy
A typical testing solution should include the following steps:
-
Create a test plan; the test plan should define the objective of testing and should include the following types of testing:
-
Hardware compatibility testing.
-
Operating system compatibility testing
-
Application compatibility testing.
-
Security testing.
-
Hardware and software assessment.
-
Performance baseline determination.
You should also document all installation, configuration and administrative processes which you are going to utilize.
-
-
Create relevant test cases; for each test case which you define, you should include the following information:
-
Purpose of the test case.
-
Hardware needed to perform the test.
-
Software needed to perform the test.
-
Necessary configuration which should be applied before the test can be performed.
-
How the test should be performed.
-
-
Build a testing environment; the testing environment which you create is determined by a number of elements, such as the size and requirements of the organization, the network infrastructure, the degree of testing which should be performed, and how much time can be set aside for testing. A testing environment or test lab can be utilized to perform a number of operations.
-
Perform the actual security configuration testing; you should evaluate and document the results of your testing.
Building a Testing Lab
The main purpose of building a testing lab is to mirror the production networking environment as far as you can.
The type of testing lab that you need to create, and how that lab is created, it determined by a number of factors, including the following:
-
The nature of the organization.
-
The requirements of the organization.
-
The size of the organization.
-
The intricacies of the network design.
-
The scope defined for testing
-
The time set aside for testing
A testing lab can be created for a number of purposes:
-
Create and test the network design for your proposed network infrastructure solution.
-
Test deployment of hardware components.
-
Test deployment of software products.
-
Test deployment of upgrades, patches, and hotfixes.
-
Test for and determine bandwidth requirements.
-
Test performance
-
Plan capacity.
-
Test and plan business procedures
-
Train users
Implementing a Test Network
After the testing lab is built, you can use it to perform actual testing. The testing process which you utilize would be based on the specifications of the test plan or test procedures.
Creating a test plan entails the following:
-
The objective of testing – what is being tested.
-
The manner in which the test should be conducted:
-
Test cases should be drawn up to analyze the components of the new network design.
-
Test whether and how the new network design works with the existing network infrastructure.
-
Test hardware compatibility
-
Test driver compatibility
-
Test application compatibility
-
For your testing lab, you should appoint a testing lab manager. The typical functions of a testing lab manager are listed here:
-
Create testing lab policies and processes.
-
Manage configuration changes to the testing network.
-
Manage the configurations of hardware and software, and of upgrades.
-
Monitor and tracking system changes and usage.
-
Manage the change control process.
-
Maintain test lab security.
-
Manage testing documentation.
Creating a Pilot Deployment
The primary objective of creating a pilot deployment is to have users perform their functions as they would normally do.
The success of a pilot deployment depends on the following:
-
The users that you select for the pilot deployment: When selecting users for the pilot deployment, you should consider the following points:
-
The type or sort of configurations being deployed.
-
The role or position of the user within the organization.
-
The capabilities and competencies of the users.
-
-
The technical support that is available for users: Your pilot deployment plan should include technical support staff for performing the following functions:
-
Support users during the pilot deployment.
-
Address issues and problems which could arise in the pilot deployment.
-
An important element to include in your pilot deployment plan is a rollback procedure. The rollback procedure should deal with restoring the network to its previous network configuration if serous issues are detected in the pilot deployment
Another important element to include in the pilot deployment plan is the training of support staff and users. Training would enable your users to utilize and work with the new network configuration.
How to build a testing tab
You can use the process below as a guideline for building a testing lab:
-
First, identify and obtain the hardware and software components for the testing lab. Hardware and software components typically include the following:
-
Network infrastructure components
-
Cabling
-
Routers
-
Switches
-
Server hardware
-
Workstation hardware
-
Operating system software
-
Applications and software products.
-
-
To simplify troubleshooting, clearly label each device and all your cables.
-
You now have to install the routers and switches, and then configure the components so that you have network connectivity for your testing lab.
-
The next step is to install the server hardware and then configure the servers according to their production roles.
-
You should configure the central processing unit (CPU) and random access memory (RAM) as you would in the production networking environment.
-
You should also configure the following elements the same as you would in the production environment:
-
Hard drive arrays
-
Partitions
-
Drive letters
-
-
-
Next, you should defragment each hard drive.
-
Install the latest antivirus software.
-
Install the operating system.
-
For Windows Server 2003 servers, it is recommended that you use a clean installation of the operating system.
-
For the upgrade of existing servers, you should test the upgrade procedure. To do this, install a copy of the existing network operating system.
-
Next, test the network connectivity achieved in your testing lab.
-
The next step is to install the application software in the testing lab which you will be using in your live production environment:
-
Install the necessary server applications
-
Install Terminal Services
-
Install management tools
-
-
The second final step is to install your client computers, and then you have to configure the client computers.
-
Lastly, secure your testing lab.

Follow Us!