An Overview on Secure Sockets Layer (SSL)
The Secure Sockets Layer (SSL) protocol was developed by Netscape Communications, and enables secure communication over the Internet. SSL works at the transport layer of Transmission Control Protocol/Internet Protocol (TCP/IP), which makes the protocol independent of the application layer protocol functioning on top of it. SSL is an open standard protocol and is supported by a range of both servers and clients.
SSL can be utilized for the following:
- Encrypt Web traffic using Hypertext Transfer Protocol (HTTP). When HTTP is utilized together with SSL, it is known as HTTPS.
- SSL is generally utilized to authenticate Web servers, and to encrypt communications between Web browsers and Web servers.
- Encrypt mail and newsgroup traffic.
SSL provides the following features for securing confidential data as it transverses over the Internet:
- Authentication
- Data integrity
- Data confidentiality through encryption
SSL works by combining public key cryptography and secret key encryption to ensure data confidentiality. The Rivest-Shamir-Adleman (RSA) public key algorithm is used to generate the certificates, and the public and private key pairs utilized in SSL. When a client Web browser connects to a Web server that is configured for SSL, a SSL handshake process is initiated with the Web server. The Web server at this stage has already obtained a server certificate from a certificate authority (CA).
A server certificate is a digital certificate which the server utilizes to verify its identity to other parties. Digital certificates form the basis of a Public Key Infrastructure (PKI) because these certificates use cryptographic algorithms and key lengths to protect data as it is transmitted over the network. The X.509 standard, derived from the X.500 directory standard, defines digital certificates. It describes a certificate as the means by which the distinguished name of the user can be associated with the public key of the user. The distinguished name of the user is defined by a naming authority. The distinguished name is used by the issuing Certificate Authority (CA) as the unique name of the user. A digital certificate contains information such as the certificate version, serial number, signature, issuer, and validity period, among other information.
A Certificate Authority (CA) can be defined as an entity that generates and validates digital certificates. The CA adds its own signature to the public key of the client. This essentially indicates that the public key can be considered valid, by those parties that trust the CA. Examples of third party entities that provide and issue digital certificates are VeriSign, Entrust and GlobalSign. Because these entities issue digital certificates for a fee, it can become a costly expense in a large organization. By using the tools provided by Microsoft, you can create an internal CA structure within your organization. You can use Windows Server 2003 Certificate Services to create certificates for users and computers in an Active Directory domain.
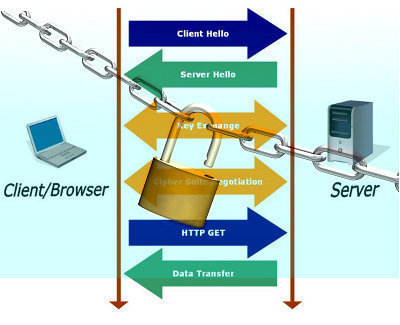
The SSL handshake process occurs between a client and Web server to negotiate the secret key encryption algorithm which the client and Web server will utilize to encrypt the data which is transmitted in the SSL session. The client Web browser initiates the handshake process by using a URL starting with the following: https://.
The SSL handshake process is described below:
- The client initiates the SSL handshake process by sending a URL starting with the following: https:// to the server.
- The client initially sends the Web server a list of each encryption algorithm which it supports. Algorithms supported by SSL include RC4 and Data Encryption Standard (DES). The client also sends the server its random challenge string which will be utilized later in the process.
- The Web server next performs the following tasks:
- Selects an encryption algorithm from the list of encryption algorithms supported by, and received from the client.
- Sends the client a copy of its server certificate.
- Sends the client its random challenge string
- The client utilizes the copy of the server certificate received from the server to authenticate the identity of the server.
- The client obtains the public key of the server from the server certificate.
- The client next generates a premaster secret. This is a different random string which will in turn be utilized to generate the session key for the SSL session. The client then encrypts a different value called the premaster secret using the public key of the server, and returns this encrypted value to the server. This is accompanied with a keyed hash of the handshake messages, and a master key. The hash is used to protect the messages exchanged in the handshake process. The hash is generated from the former two random strings transmitted between the server and the client.
- The server sends the client a keyed hash of all the handshake messages exchanged between the two parties so far.
- The server and the client then generate the session key from the different random values and keys, and by applying a mathematical calculation.
- The session key is used as a shared secret key to encrypt and decrypt data exchanged between the server and the client.
- The session key is discarded when the SSL session either times-out or is terminated.
What is Transport Layer Security (TLS)
TLS (Transport Layer Security), defined in RFC 2246, is a protocol for establishing a secure connection between a client and a server. TLS (Transport Layer Security) is capable of authenticating both the client and the server and creating a encrypted connection between the two.
The TLS (Transport Layer Security) protocol is extensible, meaning that new algorithms can be added for any of these purposes, as long as both the server and the client are aware of the new algorithms.
TLS is an internet standard version of Secure Sockets Layer (SSL), and is very similar to Secure Sockets Layer version 3 (SSLv3).
The key differences between SSLv3 and TLS are:
- You can extend TLS by adding new authentication methods.
- TLS utilizes session caching, thereby improving on SSL performance.
- TLS also distinctly separates the handshake process from the record layer. The record layer holds the data.
SSLv3 uses the Message Authenticate Code (MAC) algorithm, while TLS utilizes a hash for Message Authentication Code, also known as HMAC. Because the differences between SSL and TLC are so few, the protocols are typically called SSL/TLS. While being quite similar, SSL and TLS do not interoperate. For a secure session, both parties must utilize either SSL or TLS.
SSL/TLS has the following layers.
- Handshake layer: This layer deals with establishing the secure SSL session by negotiating key exchange using an asymmetric algorithm such as RSA or Diffie-Hellman. The handshake layer is responsible for these key elements:
- Authentication: Digital certificates are used in the authentication process managed by the handshake process.
- Message encryption: For encryption, symmetric keys (shared secret keys) and asymmetric keys are utilized. With symmetric keys, the identical key is utilized to both encrypt and decrypt data. With asymmetric keys, a public key and a private key is utilized to encrypt and decrypt data. This essentially means that two separate keys are used for message encryption and decryption.
- Hash algorithms: The hash algorithms supported are the Standard Hash Algorithm 1 (SHA1) and Message Digest 5 (MD5). SHA1 produces a 160-bit hash value, while MD5 produces a 128-bit hash value.
- Record layer: This layer contains the data, and is also responsible for ensuring that the communications are not altered in transit. Hashing algorithms such as MD5 and SHA are used for this purpose.
The benefits associated with utilizing SSL/TLS are:
- It is easy to deploy.
- Server authentication, and client authentication (optional) occurs.
- Message confidentiality and integrity are ensured.
- The parties partaking in the secure session can choose the authentication methods, and encryption and hash algorithms.
The shortcomings associated with deploying SSL/TLS are:
- SSL/TLS needs additional CPU resources to establish the secure session between the server and client.
- Because SSL/TLS utilizes certificates, you would need administrators to manage these certificates, and the certificate systems.
The different situations where an SSL/TLS implementation normally occurs:
- SSL/TLS can be utilized to authenticate client access to a secure site. You can require client and server certificates, and only allow access to the site to those clients that are authenticated.
- Applications which support SSL can require authentication for remote users logging on to the system.
- Exchange servers can use SSL/TLS to provide data confidentiality when data is transmitted between servers on the intranet or Internet.
Many protocols use TLS (Transport Layer Security) to establish secure connections, including HTTP, IMAP,POP3, and SMTP.
A Free Implementation of TLS
The OpenSSL Project is a non-commercial toolkit implementing the TLS (Transport Layer Security) protocols.
Configuring Firewalls to Allow Encrypted Traffic
To enable SSL traffic to pass through the firewall, one of two methods can be used:
- You can configure the firewall to permit all traffic with a specified port. The firewall will however only be able to use the source and destination of the SSL packets to determine whether to allow a packet to pass through. The firewall does not examine the contents of SSL packets.The common ports which applications utilize for SSL are listed below:
- Hypertext Transfer Protocol (HTTP): SSL port 443; Standard port 80
- Simple Mail Transfer Protocol (SMTP): SSL port 465; Standard port 25
- Internet Message Access Protocol (IMAP): SSL port 993; Standard port 143
- Lightweight Directory Access Protocol (LDAP): SSL port 636; Standard port 389
- Network News Transfer Protocol (NNTP): SSL port 563; Standard port 119
- Post Office Protocol version 3 (POP3) : SSL port 995; Standard port 110
- You can configure the firewall as a proxy server. In this configuration, the client establishes a session with the firewall, and the firewall establishes a session with the particular server.
A Comparison of IPSec and SSL
The Windows Server 2003 Public Key Infrastructure (PKI) is based on the following standards:
- Public key infrastructure X.509 (PKIX) standard
- Internet Engineering Task Force (IETF) standards: IETF recommends that the security standards listed below interoperate with a PKI implementation to further enhance the security in enterprise applications.
- Transport Layer Security (TLS)
- Secure Multipurpose Internet Mail Extensions (S/MIME)
- Internet Protocol Security (IPSec)
As is the case with SSL, IPSec is also utilized to ensure authentication, data confidentiality, and message integrity. A few key differences between IPSec and SSL are:
- IPSec is implemented by the operating system (OS) and is transparent to those applications utilizing it. SSL is implemented by distinct applications. While SSL cannot be utilized to encrypt all the types of data communicated between two hosts, IPSec can be utilized to secure most types of network communications.
- SSL can only be used to encrypt communications between two hosts, while IPSec can tunnel communications between networks.
- IPSec can be used to encrypt data for absolutely any application. Applications have to support SSL in order for SSL to encrypt data for the application.
- For authentication, IPSec utilizes public key certificates or a shared secret. SSL has to utilize public key certificates.
- With IPSec, the server and the client need to be authenticated. With SSL, either the server, or the client, or both the server and client needs to be authenticated. While IPSec requires each end of the connection to authenticate, SSL does not.


Follow Us!