wermgr.exe
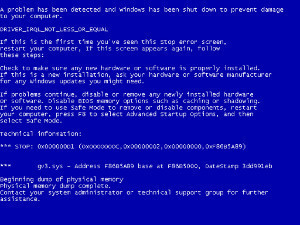
Wermgr.exe (Windows Error Reporting Manager) is a process that runs on the Windows Operating System and is responsible for running the Windows Error Reporting software when Windows crashes. Wermgr.exe is usually encountered when Windows Explorer stops working, in which case the user is presented with a message that says that Windows Explorer has encountered a …