Integrating the DNS Server with DHCP and WINS
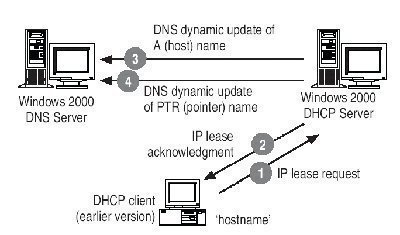
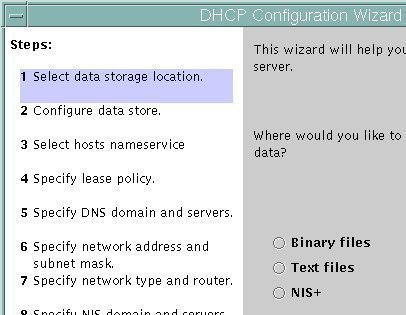
Configuring DNS Server and DHCP Integration Windows 2000, Windows XP, and Windows Server 2003 clients can dynamically update their own resource records in Windows Server 2003 DNS. DHCP can also be used to configure down-level clients as DHCP clients. To enable the DHCP server to dynamically update clients; Click Start, Administrative Tools, and then click …