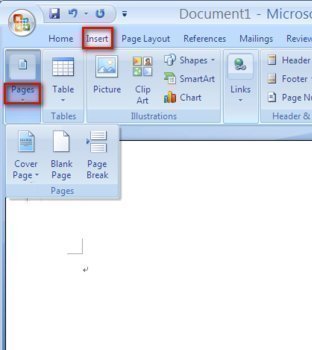
How to Add or Delete a Page in Microsoft Word
Microsoft Word is the commercial word processing program that the Microsoft Corporation created. It was first released in 1983. Since that time, the program has been upgraded to keep pace with technology and is available for use on both the Windows and OS X Operating Systems (OSs). A common task for Microsoft Word users is …