Traversing and Searching a Linear Linked List
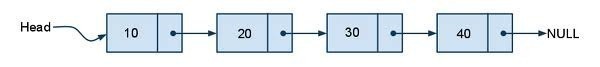
Traversing a list A linear list can be traversed in two ways In order traversal Reverse order traversal In order Traversal To traverse the linear linked list, we walk the list using the pointers, and process each element until we reach the last element. .cf { font-family: Lucida Console; font-size: 9pt; color: black; background: white; …