Type Conversion – Class to Class
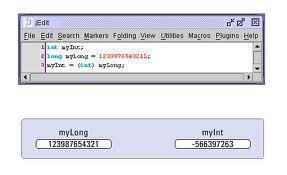
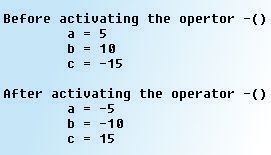
Now that we have understood how to convert basic data types to class types and vice-versa, it is time to learn how to convert objects of one class type to another class type. The conversion between objects of different classes can be done using either a one-argument constructor or a conversion function. The choice depends …