Consumers commonly mistake an intrusion detection system (IDS)with a computer firewall. Although both applications have a similar goal to protect end-users from nefarious hackers and computer malware, an IDS differs from a firewall in that it can be either a device or software program created to monitor an individual computer, computing device, or network for either security policy violations or malicious activity. Once this type of behavior is observed, the intrusion detection system makes a report to a centralized management component or station.
What is an Intrusion Detection System?
Intrusion detection systems are designed to analyze network traffic for potentially malicious behavior and to report possible “intrusions” to a centralized management node. Some IDSs are designed to take action to prevent these attempts from being successful; however, stopping malicious attacks is not a required component of an IDS. Many times, an organization will install an IDS to help document existing threats to company networks, to identify existing issues with violations of security policy, or to deter end-users from consistently violating company or organization security policies. Since IDSs were first introduced, they have become a critical component to most major organization’s security infrastructures.
Intrusion Detection Systems
The concept of an intrusion detection system dates to 1984 when Fred Cohen determined that it was possible to detect network intrusions based on information available to network administrators if enough computing resources were devoted to the task. By taking a hard look at file access logs, user access logs, and system event logs, most unauthorized network intrusions could be detected.
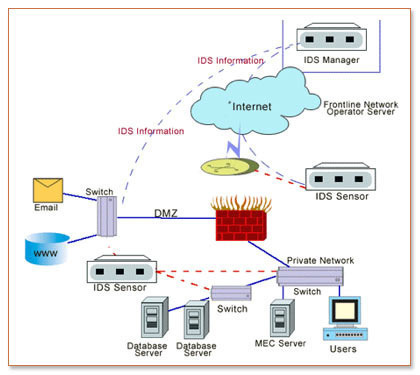
In 1986, Dorothy E. Denning assisted by Peter G. Neumann, published a new IDS model that continues to serve as the basis for intrusion detection systems in use today. Her model from the mid-1980’s made use of statistical analysis for detecting network anomalies. The resulting implementation of this work was the Intrusion Detection Expert System (IDES) implemented at SRI International that ran on Sun work stations. This implementation made use of both a rules set as well as a statistical anomaly detection systems that looked at host systems, target systems, and end-users. Later, Lunt added an artificial neural network as a third component to the system which all made reports to a resolver application. The resulting work was deployed in the Next-generation Intrusion Detection Expert System, or NIDES.
In 1988, MIDAS(Multics intrusion detection and alerting system), was released using Lisp and P-BEST for the underlying development technologies. The MIDAS work was based on the original Denning and Neumann publication and made use of statistics to reduce the overall audit trail footprint.
Following the release of MIDAS, the Los Alamos National Laboratory released Wisdom & Sense, or W&S. W&S was able to create IDS rules based on statistical analysis. These rules were then used for anomaly-based detection within the network.
Two years later in 1990, TIM (Time-based Inductive Machine) was unveiled capable of anomaly detection using inductive learning based on sequential end-user patterns. The system made use of the Common Lisp programming language and was hosted on a VAX 3500 computer. Other IDS systems that came out in this time frame included the Information Security Officer’s Assistant (ISOA) which used a number of strategies to detect anomalies to include an expert system, profile validation, and statistics; AT&T Bell Lab’s ComputerWatch which leveraged rules grounded by statistics, and in 1991 the University of California Distributed Intrusion Detection System (DIDS) that also leveraged expert systems.
The Los Alamos National Laboratory Integrated Computing Network (ICN) released NADIR (Network Anomaly Detection and Intrusion Reporter) in 1991. NADIR made use of expert systems grounded in statistics-based anomaly detection and incorporated many of the ideas published by Lunt and Denning.
In 1998, the Lawrence Berkeley National Laboratory announced the release of the Bro IDS. Bro made use of a rule language developed for the project that made use of data packet analysis from the libpcap data. A follow-on project named NFR (Network Flight Recorder) was released in 1999 that also used libpcap. Shortly after this, APE was released as a packet sniffer making use of libpcap. The APE project would later be renamed to “Snort” and has grown to become one of the most used Intrusion Detection Systems in the world at the time of this writing.
Types of Intrusion Detection Systems
There are three types of intrusion detection systems on the market today: network instruction detection systems (NIDSs), host-based instruction detection system’s (HIDSs), and stack-based intrusion detection systems (SIDS).
Network Intrusion Detection System
A network intrusion detection system analyzes network traffic and hosts to locate potential intrusions. The NIDS system connects to a network hub, network tap, or network switch that is configured to allow monitoring of network traffic. When setting up a network intrusion detection system, the monitoring points are setup at high-traffic areas on the network to examine the network data packets for potentially malicious actions.
Host-Based Intrusion Detection System
Host-based intrusion detection systems (HBIDs)are designed to have one network host agent that uses application logs, file-system modifications, and system call analysis to locate intrusions to the network. The sensors in a host-based intrusion detection system normally consist of software agent(s). A common example of a HIDS are OSSEC and Tripwire.
Stack-Based Intrusion Detection System
Stack-based intrusion detection systems (SIDS) were developed as a succeeding technology to HBIDs. SIDS examine network packets as they travel through the network stack (TCP/IP). As a result, the SIDS technology does not incur the overhead of having to communicate with the network interface in promiscuous mode.
What is the Difference Between Passive and Reactive IDSs?
When an intrusion detection system is labeled as a “passive” type, an alert will be provided on the network control console or to the owner of the system after logging the event. When an IDS is considered to be a reactive system, the IDS will respond to the potential “attack” by resetting the suspicious connection or modify the network firewall to block the suspicious network traffic. A reactive IDS is also known as an intrusion prevention system (IPS). When an IDS combines the features of both a passive and reactive system, it is referred to as an IDPS.
What are the Differences Between Statistical and Signature-Based Intrusion Detection Systems?
Statistics-based intrusion detection systems have been deployed for a number of years. This type of IDS will record normal network activity such as the types of protocols commonly used, devices connected to the network, ports used, and overall bandwidth. When network activity is detected that is out of the ordinary, the IDS will provide an alert to the network administrator or end-user regarding the event(s).
A signature-based intrusion detection system compares network data packets with pre-determined network attack patterns or signatures. Unfortunately, there can be a significant delay in identifying new threat signatures to upload to the IDS. This makes signature-based IDSs vulnerable to emerging threats.
How Does an Intrusion Detection System Differ from a Firewall?
A common misconception amongst end-users is that firewalls and intrusion detection systems are the same thing. Although both technologies help preserve network and computer security, they have distinct functions. Firewalls are designed to limit access from origins outside of the network to stop attacks from occurring. They are unable to identify malicious actions that being inside of the network. Intrusion detection systems are designed to identify attacks once they have gained access to the network and can evaluate potentially malicious actions which originate from within the network. As technologies have matured; however, a hybrid system referred to as an intrusion prevention system has been developed. The IPS is designed to stop malicious network connections and is also considered to be a firewall residing in the application layer of the OSI network model.
Limitations of Intrusion Detection Systems
Intrusion detection systems are not perfect. Depending on the design of the system, a number of false-positive results can be generated. These “false alarms” can originate from bad software, corrupt domain name server information, or local network traffic. As a result, a real network attack can be missed if the IDS is not properly configured for the defended network. Another vulnerability of IDSs that rely on signature files is updating the signature library to include the latest threats. When left undone, the network can be open to attack from the most current threats.
Free Intrusion Detection Systems
There are several freely available intrusion detection / prevention systems available on the marketplace today. Some of the better known projects include Snort, File System Saint, and AIDE.
Snort
One of the most downloaded and installed intrusion detection and prevention systems in the world today is Snort. Originally published in 1998 by CTO Martin Roesch, the application is designed to perform real-time packet logging and traffic analysis on IP-based networks. At the time of this writing, Snort has been downloaded more than four million times since initial release and has more than 400,000 registered users of the software. The application is based on a rule-based language that combines several additional IDS technologies to include protocol, anomaly-based, and signature detection methods.
File System Saint
File System Saint (FSS) is another open source intrusion detection system written in the Perl programming language. The software project is designed to be lightweight, fast, and easy to use. FSS works on the basic premise of storing an image of the live file system of the network being protected and analyzes the system for any changes to the baseline report. The application also stores data about file owner, permissions, file size, mtime, and ctime and reports changes to the computer owner via email report. To guard against tampering, FSS saves a cryptographic hash file to ensure legitimate data is being used while in operation.
AIDE
AIDE (Advanced Intrusion Detection Environment) is deployed as a free replacement for the commercially available Tripwire IDS. The software application is designed to check the integrity of the system’s file and directories. To achieve this functionality, AIDE creates a database from the regular expression rules contained in the software’s configuration files. After the database is created, it is used to validate the file integrity of the protected computer. Additional application features include support for the following message digest algorithms: sha1, rmd160, md5, crc32, sha256, sha512, tiger, and whirlpool. AIDE also supports gzip database compression if zlib support is installed on the protected computer.


Follow Us!