A firewall is a software component that restricts unauthorized inward network access. It allows outward information flow. It is set up to control traffic flow between two networks by configured permissions like Allow, Deny, Block, Encrypt, etc. It is normally employed to avoid illegal access to personal computers or corporate networks from external unsafe entities like the Internet.
The firewall scrutinizes all the information flowing in and out of the network. If some data do not meet the necessary criterion, it is denied access into the network. A firewall’s key function is to legalize the stream of traffic among computer networks of different trust levels. Similar to the physical firewalls installed in buildings that help limit the spread of fire, the software firewalls also help control network intrusions. A poorly configured firewall is useless. By default, the “deny” rule-set should be applied and allow only those applications to communicate for which the permissions have been explicitly set to “Allow.” However, such configurations require expertise understanding. Due to the lack of such expertise understanding, many corporate networks keep “Allow” as their default rule-set.
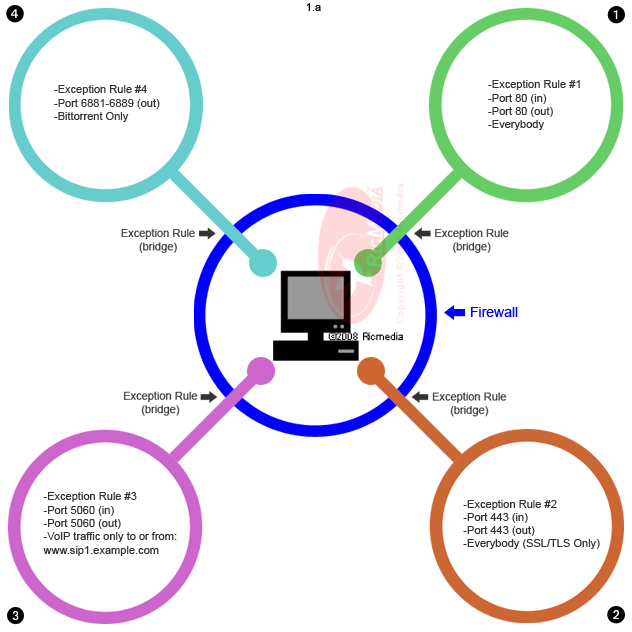
There are numerous firewall scrutiny techniques. An easy technique is to examine the incoming requests to make sure they arrive from trusted (formerly recognized) domain name and networks. Many companies develop firewall software. Firewall software features comprise of logging and reporting, routine alerts at specified points of intrusion, and a graphical user interface for managing the firewall software.
Types of Firewalls
The most basic firewall classifications falls into Hardware firewalls or Software firewalls. Hardware firewalls are considered external to the system, whereas Software firewalls are internal.
- Hardware FirewallsHardware firewalls are normally situated between the network and the connecting cable/modem. These are external hardware devices usually called Network firewalls. Many a times, network devices called ‘Routers’ include firewall security. Hardware firewalls provide a high external defense level from intrusions since they are separate devices and possess their own operating environment, offering an extra line of defense.
Software firewalls use becomes less important if a strong Hardware firewall is implemented. The main fallback for Hardware firewall is they are quite expensive when compared to Software firewalls.
- Software FirewallsSoftware firewalls are basically software components that are internal to the computer system. They work hand-in-hand with the computer’s operating system. Nowadays, many operating systems are shipped with an inbuilt software firewall. Numerous firewall packages that various companies develop are on the market.
The disadvantage to software firewalls is that they will only guard the computer they are installed on, not the entire network. Hence, it necessitates every computer to have a software firewall installed on it. They are comparatively less expensive then the Hardware firewalls.
How Firewalls Work
Different kinds of firewalls function differently. They scrutinize, examine, and control the network traffic in numerous ways depending on their software architecture. Below are firewalls that work in different ways:
- The Packet Filtering Firewall
One type of firewall is the packet filtering firewall. In a packet filtering firewall, the firewall examines five packetcharacteristics:1. Source IP address
2. Source port
3. Destination IP address
4. Destination port
5. IP protocol (TCP or UDP)Based upon rules configured into the firewall, the packet will either be allowed through, rejected, or dropped. If the firewall rejects the packet, it sends a message back to the sender letting him/her know that the packet was rejected. If the packet was dropped, the firewall simply does not respond to the packet. The sender must wait for the communication to time out. Dropping packets instead of rejecting them greatly increases the time required to scan the network. Packet filtering firewalls operate on Layer 3 of the OSI model, the Network Layer. Routers are a very common form of packet filtering firewall.
An improved form of the packet filtering firewall is a packet filtering firewall with a state oriented inspection engine. With this enhancement, the firewall “remembers” conversations between systems and networks. It is then necessary to fully examine only the conversation’s first packet.
- The Application-Proxy Firewall
Another type of firewall is the application-proxy firewall. In a proxy based firewall, every packet is stopped at the proxy firewall. The packet is then examined and compared to the rules configured into the firewall. If the packet passes the examinations, it is recreated and sent out. Because each packet is destroyed and recreated, there is a potential that an application-proxy firewall can prevent unknown attacks based upon weaknesses in the TCP/IP protocol suite that a packet filtering firewall would not prevent. The drawback is that a separate application-proxy must be written for each application type being proxy examined. An HTTP proxy for web traffic, an FTP proxy for file transfers, a Gopher proxy for Gopher traffic, and so on are needed. Application-proxy firewalls operate on Layer 7 of the OSI model, the Application Layer.
- The Application-Gateway Firewall
Application-gateway firewalls also operate on Layer 7 of the OSI model, the Application Layer. Application-gateway firewalls exist for only few network applications. They intercept and examine all the information traveling from application to application. A typical application-gateway firewall is a system where the user must telnet to one system in order to telnet again to a system outside of the network.
- The SOCKS Firewall
Another type of application-proxy firewall is the SOCKS firewall. Where normal application-proxy firewalls do not require modifications to network clients, SOCKS firewalls require specially modified network clients. This means users have to modify every system on their internal network that needs to communicate with the external network. On a Windows or OS/2 system, this can be as easy as swapping a few DLLs.

Shaharyar Khan
i am grateful to you sir for writing this article , it is to much helpful for my work…..
paolo brambilla
vorrei aprire facebook ma mi esce la scritta sito bloccato da firewall neatgear cosa posso fare per aprire facebook?
Vishal Bedre
This web page give me basic information about firewall. It also give clear concept of what the exact firewall is. Thank you!
Vishal Bedre
Can you provide me price for some of the firewall. Thank you!
vishalbedre2007@gmail.com
SmallFish
Great article – Quick question. I am changing from one provider to another (XO to at&t) thus at&t will be bringing in a new circuit (VoIP) and providing a managed router. From what I understand, the router does not provide firewall functionality. I have an external firewall (Safeoffice). Is it as simple as connecting the cable from the router into the firewall or do I need to make changes to my firewall? Thanks.
Will.Spencer
Depending upon the firewall configuration, you might have to change some of the IP addresses in your ruleset. Other that that, it should work perfectly.
SmallFish
Thanks for the response. I received a gateway/router IP address and then 5 “useable” ip addresses. I am assuming I need to put the gateway address in and one of the other ip addresses for my firewall. Is there a simple command line input that I use to make these changes?
prathyusha
this article is very informative and can be understood well
Gaurav Bajpai
Hi,
This article is realy very informative.
Gaurav Bajpai 😆