VLAN Hopping
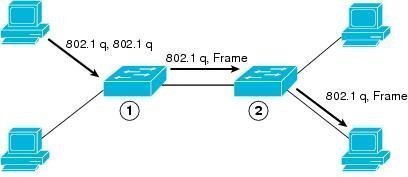
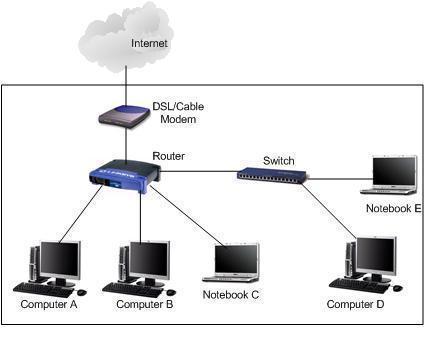
VLAN Hopping is one of the primary VLAN based attacks used by hackers to infiltrate network security. VLAN hopping is used to attack a network by sending packets to a port which is generally not accessible. VLAN hopping attacks are mainly conducted in the Dynamic Trunking Protocol and, in some cases; the attacks are targeted …