PKI Authorities consists of three different authorities that essentially make up a PKI system. These are the Registration Authority, Certification Authority and Certificate Directory.
Registration Authority
The jobs of the Registration Authority are to processes user requests, confirm their identities, and induct them into the user database.
Certification Authority
The tasks of a Certification Authority are to issue public key certificates and to attest that the public key embedded in it indeed belongs to the particular entity as stated in the certificate. The Certification Authority also has the right to cancel a certificate if required, and verify it at any point of time depending on the registration conditions. 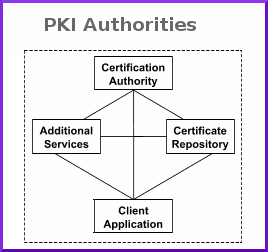
Certificate Directory
The Certificate Directory manages and stores the user’s registration information and certificates for future references.
From the above mentioned logical structuring of the different authorities, it is quite clear that the success of any public key infrastructure system depends entirely upon the efficiency, coordination, and performance of its public key infrastructure system authorities.
Alternatives to PKI Authorities
Alternatives to PKI authorities include: Web of Trust, Simple Public Key Infrastructure (SPKI) and Robot Certificate Authorities.


Follow Us!