Certificate Authority or Certification Authority (CA) is an entity, which is core to many PKI (Public Key Infrastructure) schemes, whose purpose is to issue digital certificates to use by other parties. It exemplifies a trusted third party. Some certification authorities may charge a fee for their service while some other CAs are free. It is also not uncommon for government and institutions to have their own CAs.
More about Issuing a Certificate
The certification authority issues a Public Key Certificate (PKC), which attests that the public key embedded in it indeed belongs to a particular person, server, organization or any other entity as said in the certificate. In such schemes, the obligation or duty of CAs is to verify the credentials of the applicants before issuing the certificate so that the users can trust the information in the CA certificates of a particular entity without any second thoughts.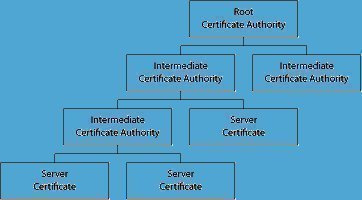
But this model is not fool proof, at least in a theoretical point of view. For example, if a person (say A) could manage to get a certification authority to issue a false certificate tying another person (say B) to a wrong public key, whose corresponding private key is available to A, then this could lead to some serious security problems. That is, if a third person (say C) eventually obtains and uses the public key in this certificate, then with the private key, it is possible for A to break into the security contours of C’s communication. In such a way, on a practical level, C’s messages could be decrypted and the person could be duped to accept forged signatures.
Security
As mentioned above, while the correctness of a certificate is taken for granted, it is to be accepted that assuring the correctness of data presented by companies, person or programs seeking a certificate is rather difficult and has glaring loop holes. That is, it is not an impossible task for an applicant to dupe the certification authority. In order to plug these chinks in the armor, certification authorities usually use a combination of authentication techniques which include leveraging government bureaus, third parties databases and services, the payment infrastructure, and custom heuristics to analyze the trust worthiness of the applicant. In few enterprise systems, local types of authentication like Kerberos can be used to obtain the certificate, which in turn can be used by relying third parties. Notaries may be required in some cases to personally verify the party whose sign is being notarized.
The Twist
In large scale deployments, it is possible to come across a situation in which two entities may have different certificates issued by separate certification agencies, and both not being familiar with each other’s CA. In order to simplify this confusion, the certificate of each entity deliberately carries a public key of its certification authority, signed by another certification authority, assuming that the second CA might be recognized by the other party. Even though this does not guarantee a complete success, it may eventually lead to a hierarchy or mesh of certification authorities and certificates, which can be confusing to an extent.

Ravi
windows always complaints about certificate authorization of google and yahoo. How can I remove the complaints and get the certificates recognized properly.