-
-
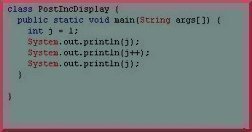
IC Design
In the modern world of data and information, computer systems need circuits that are able to process and transfer that information. Because of this, a great deal of resources and innovation go into creating more advanced circuitry in order to increase data transfer rates and make computer systems smaller. This article will demonstrate how integrated …
-
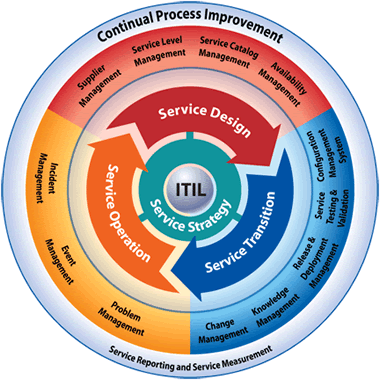
ITIL Processes
The Information Technology Infrastructure Library (ITIL) is a series of books that contain proper procedures to handle situations that any IT organization would come in contact with. Using a series of check lists, tasks and procedures, an IT organization can take what is available to it and implement it in such a way that ensures …
-
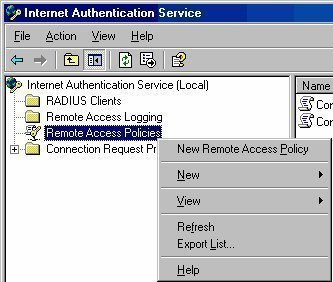
Remote Access Security
Remote Access Security Overview To protect your corporate data from attacks from intruders and from being accessed by unauthorized users, you need to plan for and implement remote access security. You should authenticate remote access clients attempting to establish a remote connection with the remote access server. To secure connections to the corporate network, you …
-
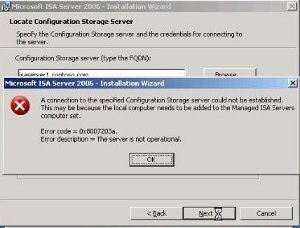
Troubleshooting ISA Server
Tools for Troubleshooting ISA Server There are a variety of tools that you can use to troubleshoot ISA Server. The type of issue would determine which of the tools(s) listed here you need to use: ISA Server Reports tool: You can use the reporting feature included with ISA Server to obtain and view information on …
-
Convert MM to Inches
Convert MM to Inches Automatically To convert MM to Inches, enter the number of MM to be converted into the MM box below. MM: Millimeters (mm) Results: Inches (in) 0 Feet (ft) 0 Yards (yd) 0 Rods (rd) 0 Miles (mi) 0 Micrometers (µm) 0 Centimeters (cm) 0 Meters (m) 0 Kilometers (km) 0 Convert …
-
VoIP Security
Any technology that involves transfer of data or information is prone to compromised security. It happens with telephones, cell phones, email and Internet transactions. Because VoIP (Voice Over Internet Protocol) has the Internet as its mode of transference it’s possible to have your Internet-based called intercepted. To make matters worse, there are techno-troublemakers who are …
-
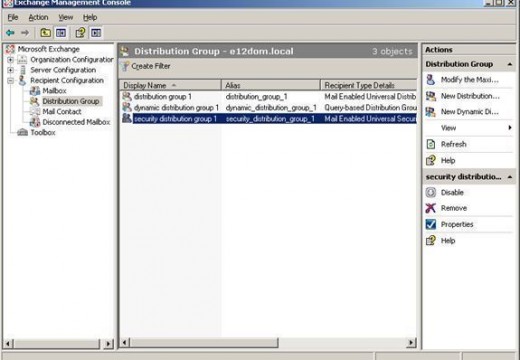
Managing Recipient Objects, Address Lists, and Distribution and Administrative Groups
Recipient Objects Overview Active Directory objects such as user accounts, contacts and groups become recipient objects when e-mail address information is added to the object. The public folder is another type of recipient object. A public folder does not however usually have its own an email address. Exchange Server 2003 supports the following types of …
-
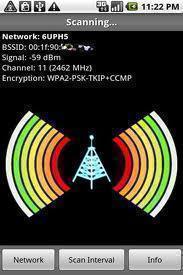
WiFi Signal Strength Meter
Windows and other operating systems have a WiFi signal strength meter, but this is usually basic software and does not really tell the user much about the wireless signal. Fortunately, there are many other programs that do the same thing, but show the user more details about the wireless connection. We will describe some of …
-
How to Dry Out a Cell Phone
When dealing with a wet phone, it is important to act quickly. Few phone companies offer a warranty on wet phones and have gone as far as to place a "wet strip" on the phone that changes colors when it has gotten wet. What this means is that the wet strip will allow the company …