Wireless Connection Security
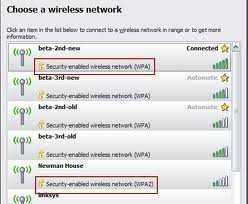
Wireless Network Security Threats Wireless networks do not have the inbuilt physical security of wired networks, and are unfortunately more prone to attacks from intruders. Once unauthorized access is gained to the wireless network, the intruder would be able to easily access the resources of the corporate, internal network. To complicate matters, there are numerous …