The Zeus Virus is the popular term for the Zeus banking Trojan virus which was used to steal bank account details and passwords in the U.K. This resulted in a loss of more than $850,000 for those infected. The Zeus virus has been around for a number of years as part of the larger Zeus Crimeware Toolkit. In 2013, the virus became news again when a new version of it resurfaced, and infected a large number of Facebook users.
The Zeus Crimware Toolkit was created by the Russian Business Network and is available for purchase through rogue hacking forums across the Internet. Criminals who purchase the Zeus Crimeware kit are given a web interface panel to control the deployment and use of the Trojan as well as an additional tool to create new Trojan binary files and encrypt the configuration file used by the virus. Other names that the Zeus Virus are known by include: PRG, NTOS, Zbot, and WSNPOEM.
Besides individual users, who shouldn’t underestimate the risk, at particular risk are small and medium sized businesses who generally have much more funds that could be targeted for theft, but often weaker security than larger companies. Strong security precautions, as well as training of employees, should be undertaken to prevent infection and ultimate loss of funds to these cybercriminals.
How Does the Zeus Virus Infect a Computer?
The Zeus Trojan infects computers in one of two ways: infected email attachments, and infected computer downloads. Particularly nasty with the Zeus Trojan is that deployments of the malware infect otherwise legitimate sites as one means of delivery to targeted computers. Links to infected downloads may be distributed through fake Facebook profiles and pages, which is how many Facebook users were infected.
When a computer is initially infected, the Trojan will create a folder in, “%windir%\system32\wsnpowem” where it will save “audio.dll” and “video.dll.” These files are then used to save information stolen from the computer under attack as well as the the configuration file that is downloaded after infection. The folder will then be hidden by the Trojan after creation. Next, the virus will copy itself to “ %windir%\system32\ntos.exe” and in certain modifications of the virus will rename itself to “oembios.exe” in the same location. After this step, the virus will check the running processes on the computer for active computer firewalls. If there are none, it will then conduct registry modifications in order to run the malware on computer start-up and continue to spread throughout the computer.
The 2013 variant of Zeus also includes an autoupdater for itself, and the ability to self-propagate through removable drives (such as memory sticks). It searches for removable drives in the computer, then creates a hidden folder, copies itself into that folder, and creates a shortcut pointing to the hidden copy. In the process of copying itself it may also alter its signature, which anti-malware products use to recognize viruses, allowing it to escape identification.
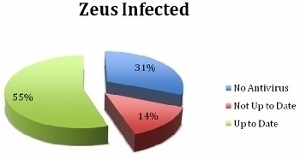
How Does Zeus Steal Data?
The Zeus Trojan is designed to steal sensitive banking information and then upload it to a secure, remote server identified in the virus configuration file. The file also identifies websites for the Trojan to target for infection to help further spread itself. After infection, Zeus will capture information entered onto on-line banking sites and sends this to the remote server. Some variants of the Trojan are able to display fake web pages for banking as an alternative option to directly stealing the data from the webform entry. The Trojan also includes the capability to take screenshots and intercept passwords for FTP and POP3 email accounts.
Removing the Zeus Virus
Step 1 – Disable System Restore on your computer. To do so, choose the “Start,” “Settings,” and “My Computer” icons. Then, select “Properties” and the “System Restore Tab.” Click “Turn off System Restore” on all drives. Choose the “Apply,” “Yes,” and “Ok” menu buttons to confirm the change in status. *Note, after removal of the Zeus virus, you will need to turn System Restore On.
Step 2 – Restart the computer in Windows Safe mode by depressing the “F8” key during normal restart. Choose the subsequent menu option “With Networking” when prompted.
Step 3 – Update your computer antivirus program definitions. The majority of commercial antivirus programs will have an option to do so on the primary antivirus program control panel.
Step 4 – Run a complete antivirus scan of all of your computer’s drives.
Step 5 – Open Windows Explorer by depressing the “Windows” and “E” keys simultaneously. Then, enable viewing of hidden files by selecting the “Tools,” and “Folder Options” menu choices. Select the “View” menu tab and click “Show Hidden Files and Folders.”
Step 6 – For each of the variants of Zeus, navigate to the location and verify the associated files are deleted. If they are not, delete the files.
Zeus Variant1:
WINDOWS\system32\ntos.exe
WINDOWS\system32\wsnpoemaudio.dll
WINDOWS\system32\wsnpoemvideo.dll
Zeus Variant2:
WINDOWS\system32\oembios.exe
WINDOWS\system32\sysproc64\sysproc86.sys
WINDOWS\system32\sysproc64\sysproc32.sys
Zeus Variant3:
WINDOWS\system32\twext.exe
WINDOWS\system32\twain_32local.ds
WINDOWS\system32\twain_32user.ds
Zeus Variant4:
WINDOWS\system32\sdra64.exe
WINDOWS\system32\lowseclocal.ds
WINDOWSsystem32lowsecuser.ds
Step 7 – Ensure registry entries made by the Zeus Trojan have been removed. To open the registry, select the “Start” and “Run” menu buttons followed by entering “REGEDIT” followed by the “Enter” key. If the following entries exist, delete by single clicking the entry followed by clicking the “delete” key.
In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run – “userinit” = “%System%\ntos.exe”
In HKEY_USERS.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Run – “userinit” = “%System%\ntos.exe”
In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\NTCurrentVersion\Network – “UID” = “[COMPUTERNAME]_[UNIQUE_ID]”
In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer – “{6780A29E-6A18-0C70-1DFF-1610DDE00108}” = “[HEXADECIMAL VALUE]”
In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer – “{F710FA10-2031-3106-8872-93A2B5C5C620}” = “[HEXADECIMAL VALUE]”
In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run – {Random} = “%Application Data%”\{Random Folder 1}\{Random Filename}.exe
In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List – “%Windows%”\explorer.exe = “%Windows%”\explorer.exe:*:Enabled:Windows Explorer
Step 8 – Exit the Registry and restart your computer normally. After the system has restarted, turn Windows System Restore on and the Zeus virus will be removed.
Also check out Trend Micro’s threat encyclopedia entry about WORM_ZBOT.GJ for more information.
Zeus Removal Tools
AVG offers a free tool that can scan for and remove the Zeus malware from your computer. It’s worth giving it a try. Additionally, other tools are available for removing Zeus as suggested by MalwareTips, which recommends running all of them to make sure you don’t miss it, and then double check your machine.

MACO
Hello can you teach me about Virus?