Kerberos is a network authentication protocol which utilizes symmetric cryptography to provide authentication for client-server applications.
Kerberos Standard Definition
Kerberos is defined in RFC 1510 – The Kerberos Network Authentication Service (V5).
Kerberos Architecture
The core of Kerberos architecture is the KDC (Key Distribution Server). The KDC stores authentication information and uses it to securely authenticate users and services.
This authentication is called secure because it:
- Does not appear as plaintext
- Does not rely on authentication by the host operating system
- Does not base trust on IP addresses
- Does not require physical security of the network hosts
The KDC acts as a trusted third party in performing these authentication services.
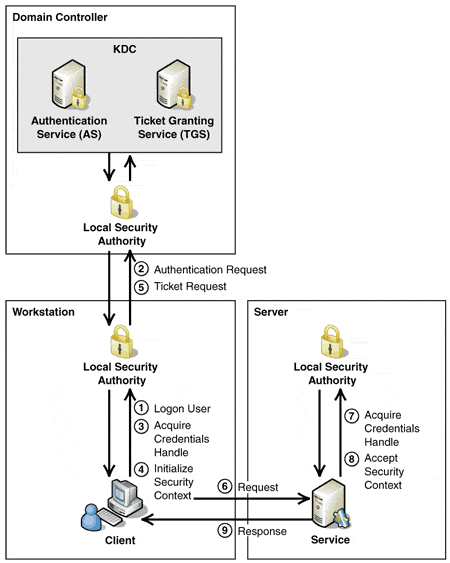
Due to the critical function of the KDC, multiple KDCs are normally utilized. Each KDC stores a database of users, servers, and secret keys.
Kerberos client applications are normal network applications modified to use Kerberos for authentication. In Kerberos slang, they have been Kerberized.
How Kerberos Works
One of the problems that comes with using a network that requires authentication from the user–a username and password–is the fact that the password is sent over the network as plain text. So, the user types in the username and password, which might appear as asterisks, and then they hit enter to submit it. The password and username travel over the network as plain text. 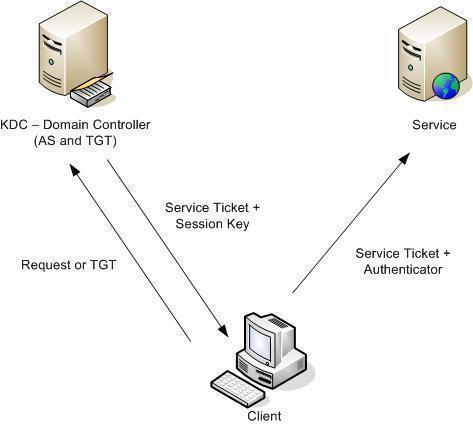
For someone looking to gain access to this information, it would not be too difficult to catch the password and username while en route through the network and use it to access the system. Kerberos allows for the password and username to be used without having to send them over the network. In other words, the network can be accessed, but the password and username don’t have to travel through it.
In a kerberized network, the kerberos database contains principles and their keys. All of the services are also stored on the kerberos database with their keys.
When a user wants to log in to the network, the principle is sent to the key distribution center (KDC). This is sent as a request for the ticket granting ticket (TGT). The request can be sent by a login program or by a kinit program.
If the KDC finds the principle in the database, it creates a TGT, encrypts it using the TGT, encrypts it using the user’s individual key and then sends it back to the user.
Once it [TGT] is received by the user, the login program decrypts the encrypted key. This TGT is stored in the credentials cache and expires after a certain amount of time. The time varies, but is typically around eight hours. This brings more security because when the TGT expires, access to the network expires as well (because a new TGT is needed).
The Kerberos Protocol
Kerberos defines ten messages that make up the Kerberos protocol:
KRB_AS_REQ Kerberos Authentication Service Request KRBAS_REP Kerberos Authentication Service Reply KRB_AP_REQ Kerberos Application Request KRB_AP_REP Kerberos Application Reply KRB_TGS_REQ Kerberos Ticket Granting Service Request KRB_TGS_REP Kerberos Ticket Granting Service Reply KRB_SAFE Kerberos Safe (Checksummed) Application Message KRB_PRIV Kerberos Private (Encrypted) Application Message KRB_CRED Kerberos Credentiials KRB_ERROR Kerberos Erro
Kerberos Implementations
MIT Kerberos is the reference implementation. MIT Kerberos supports DEC Unix, Linux, Irix, Solaris, Windows and MacOS.
Several other commercial and non-commercial Kerberos implementations are also available.
Microsoft added a slight modified version of Kerberos v5 authentication in Windows 2000.
Kerberos Weaknesses
Since KDCs store secret keys for every user and server on the network, they must be kept completely secure. If an attacker got administrative access to the KDC, he would have access to the resources of the Kerberos realm.
Kerberos tickets are cached on the client systems. If an attacker gains administrative access to a Kerberos client system, he can impersonate the authenticated users of that system.
Additional Reading on Kerberos
RFC 1510 is an excellent source for understanding the Kerberos protocol.
The Kerberos FAQ provides more information.




shifan mohamed
Kerberos is one mechanism used for authentication in network operating system security. Describe the principles of its operation.