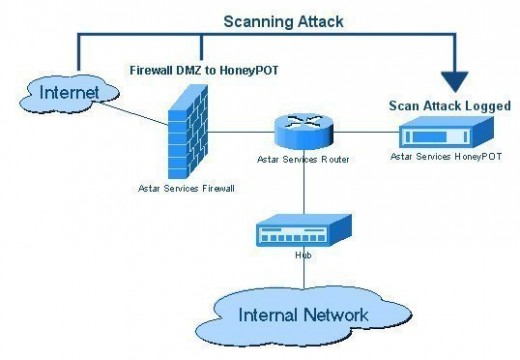
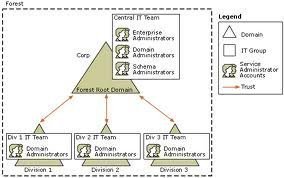
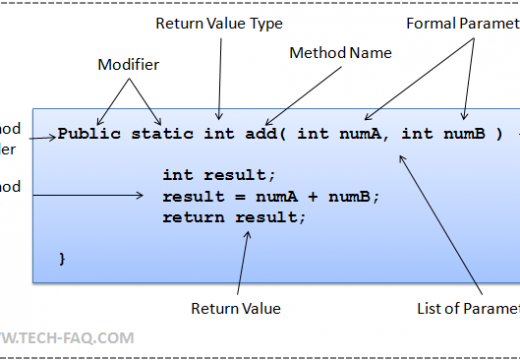
Honey Monkey
Honey monkeys are a new way of detecting malicious codes from websites that try to exploit certain vulnerabilities of Internet browsers. The honey monkey system works as an automated web/internet patrol system that is designed to detect harmful materials in the Internet, to be able to come up with solutions, and to catch the people …