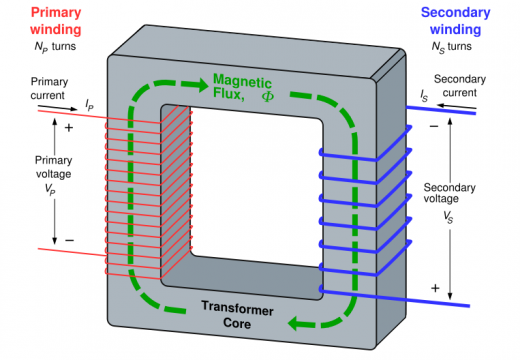
Transformer
A transformer transfers electrical energy between two circuits. It usually consists of two wire coils wrapped around a core. These coils are called primary and secondary windings. Energy is transferred by mutual induction caused by a changing electromagnetic field. If the coils have different number of turns around the core, the voltage induced in the …