L2TP (Layer Two Tunneling Protocol) defines an extension to PPTP (Point-to-Point Tunneling Protocol) that an ISP (Internet Service Provider) uses to allow a VPN (Virtual Private Network) to operate. L2TP combines L2F from Cisco Systems’ optimum features and PPTP from Microsoft into a single protocol. L2TP’s two primary components are the LNS (L2TP Network Server) that terminates and authenticates the PPP stream and the LAC (L2TP Access Concentrator) that physically terminates a call.
How does L2TP Work?
The L2TP initiates a tunnel between an LAC and an LNS on the Internet to enable a Point-to-Point Protocol (PPP) link layer to be encapsulated and then carried across the Internet. An end-user initiates a PPP connection to an ISP through either an ISDN or PSTN service. The LAC accepts the connection and establishes the PPP link. During this process, the respective ISP conducts partial authentication in order to gain the connected user’s user name. This information can then be used to grant access based on the user. A free slot within the network tunnel is then assigned and the connection request is passed to the LNS, which accepts or rejects the connection. The connection request may also include authentication information to pass to the LNS for final authentication of the connection. If the connection is accepted, a virtual PPP interface is created and link layer frames can now be passed over the established tunnel. The LNS accepts frames from the connection and then strips off the L2TP encapsulation and processes them as normal incoming frames.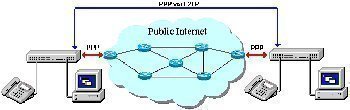
What is the L2TP Packet Structure?
The L2TP/IPSec packet structure is setup in the following order:
IP Header | IPSec ESP Header | UDP Header | L2TP Header | PPP Header | PPP Payload | IPSec ESP Trailer | IPSec Authentication trailer
What are the Uses of L2TP?
The L2TP protocol is primarily used to integrate multi-protocol dial-up services into an existing ISP point of presence. The protocol is commonly used for reselling ADSL endpoint and cable network connectivity by sitting between the end-user and the ISP. As a result, the reselling cable provider does not appear to be the one doing the transport.

Follow Us!