If ‘service password-encryption’ is not configured on the Cisco device, simply read the plain text passwords from the configuration file.
If ‘service password-encryption’ is configured on the Cisco device, most of the passwords are encrypted with a weak encryption algorithm (Type 7) that is easy to decrypt. Once there is access to the Cisco configuration file, the passwords can be decrypted fairly easily.
‘service password-encryption’ is enabled using the following command:
TopBits-Cisco (config)#service password-encryption
Network administrators often store IOS configuration files on TFTP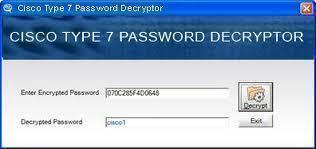
(Trivial File Transfer Protocol) servers. One server may have the
configuration files for every Cisco device on the network.
Cisco Password Encryption
Cisco uses two encryption methods to secure IOS passwords. The first, type 7, uses a Cisco proprietary weak encryption algorithm. The second, type 5, uses strong MD5 encryption.
Cisco Type 7 passwords
A password in the configuration file with a ‘7’ in the second to last field is encrypted with Cisco’s weak proprietary algorithm. For example:
enable password 7 03003E2E05077C4F4007
There are many programs that decrypt Cisco type 7 passwords.
Here is a small PERL program to decrypt Cisco type 7 passwords:
#!/usr/bin/perl -w
# $Id: ios7decrypt.pl,v 1.1 1998/01/11 21:31:12 mesrik Exp $
#
# Credits for original code and description hobbit@avian.org,
# SPHiXe, .mudge et al. and for John Bashinski
# for Cisco IOS password encryption facts.
#
# Use of this code for any malicious or illegal purposes is strictly prohibited!
#
@xlat = ( 0x64, 0x73, 0x66, 0x64, 0x3b, 0x6b, 0x66, 0x6f, 0x41,
0x2c, 0x2e, 0x69, 0x79, 0x65, 0x77, 0x72, 0x6b, 0x6c,
0x64, 0x4a, 0x4b, 0x44, 0x48, 0x53 , 0x55, 0x42 );
while (<>) {
if (/(password|md5)s+7s+([da-f]+)/io) {
if (!(length($2) & 1)) {
$ep = $2; $dp = "";
($s, $e) = ($2 =~ /^(..)(.+)/o);
for ($i = 0; $i < length($e); $i+=2) {
$dp .= sprintf "%c",hex(substr($e,$i,2))^$xlat[$s++];
}
s/7s+$ep/$dp/;
}
}
print;
Cisco Type 5 passwords
Enable secret passwords are hashed using the MD5 (Message Digest 5) algorithm instead of the weak Cisco proprietary algorithm. Enable secret passwords are not trivial to decrypt.
An “enable secret” password is configured using the following command:
TopBits-Cisco (config)#enable secret password
A password in the configuration file with a ‘5’ in the second to last field is hashed using the MD5 algorithm. For example:
enable secret 5 $1$B8pH$PmmcMRoqfeEtQ7WxL865a0
Although MD5 is a strong algorithm, it may still be attacked with a dictionary attack or a brute force attack.



etta.bartlett2
=
strick
I need to put new password on my router forgot old one how do I do that