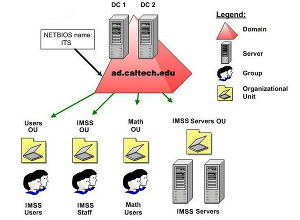
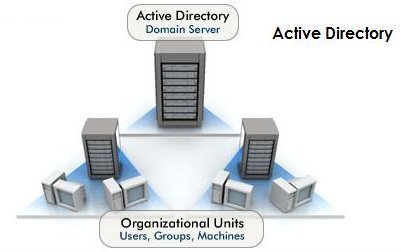
Backing Up and Restoring Active Directory
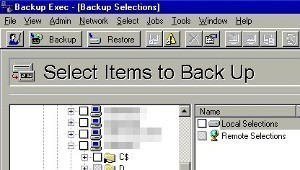
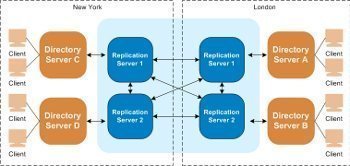
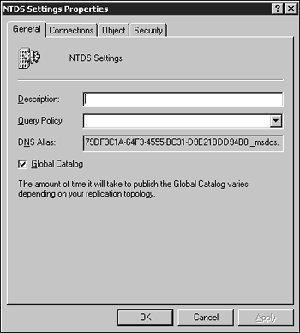
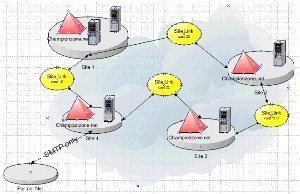
An Overview on Backing up and Restoring Active Directory To ensure availability of mission critical resources and network objects, and business continuity, you would need to perform back ups of Active Directory if it is running in your environment. This is because Active Directory normally hosts mission critical data, and resources. Backups are typically preformed …