Troubleshooting Active Directory Availability
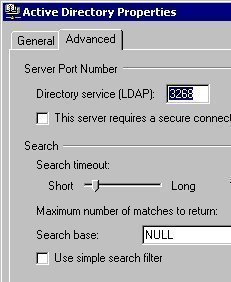
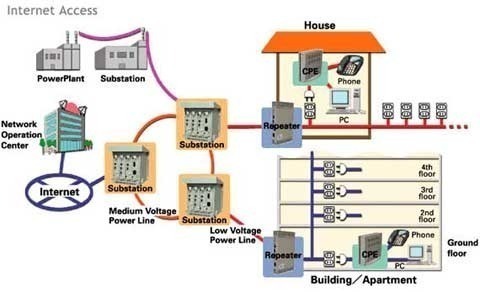
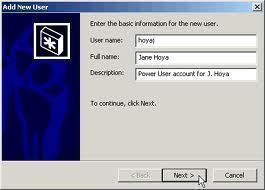
As an Administrator, ensuring the availability and reliability of the Windows Server Active Directory directory service is extremely important if you are running Active Directory within your environment. Performance problems and poor availability leads to users being unable to perform their tasks or duties within the organization. For instance, when a DNS server fails, it …