Understanding and Implementing Smart Card Authentication
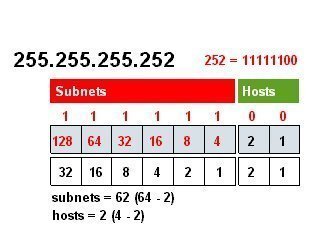
An Overview on Authentication and Smart Cards Administrators have to secure the network from attacks launched by hackers, spies, terrorists, thieves and criminals. Security encompasses numerous technologies, protocols, standards, policies, passwords, and secret keys. All these mechanisms typically focus on the following: Authentication Access Control Data Protection Auditing/Accountability Authentication is the process by which an …