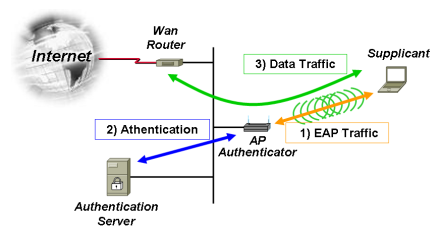
Network Attacks
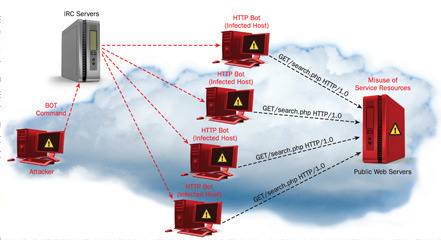
Understanding Network Attacks A network attack can be defined as any method, process, or means used to maliciously attempt to compromise network security. There are a number of reasons that an individual(s) would want to attack corporate networks. The individuals performing network attacks are commonly referred to as network attackers, hackers, or crackers. A few …