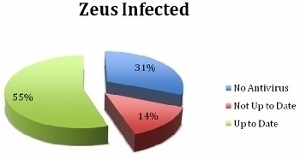
How to Connect an Xbox 360 to a Laptop
In order to connect an Xbox 360 to a laptop, the user must have an Ethernet cable. An Ethernet cable may or may not come with the Xbox 360 upon purchase, but is required to provide the Xbox 360 with an Internet connection. Normally, an Ethernet cable would be connected from the Xbox 360 to …