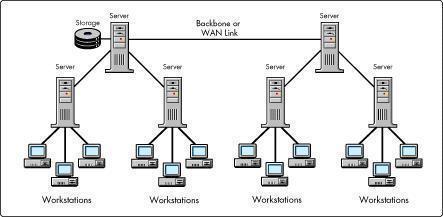
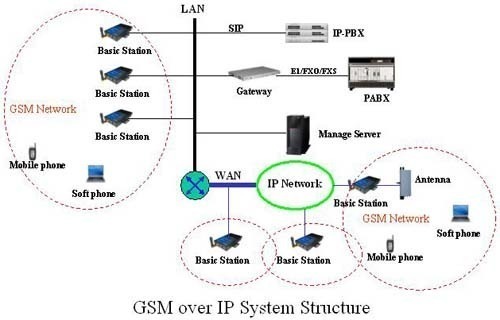
What is a Biometric Coprocessor?
A biometric coprocessor is a device that is capable of scanning a user’s physical attributes in order to allow access to a building or computer network. A biometric coprocessor is essentially a fingerprint reader, but may also include sensors that analyze the user’s eyes, voice, or even breath. The term “biometric coprocessor” comes from the …