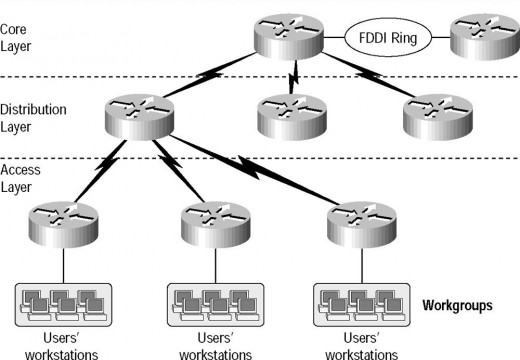
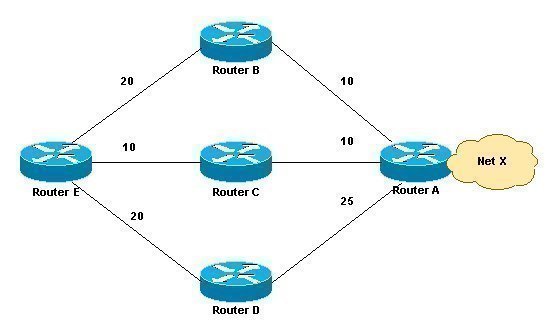
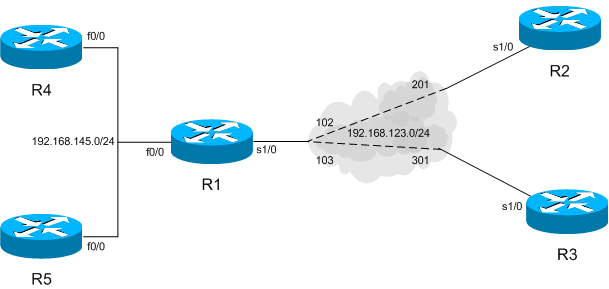
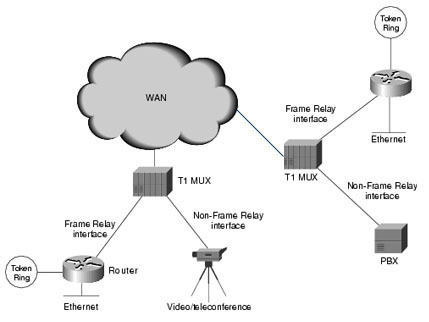
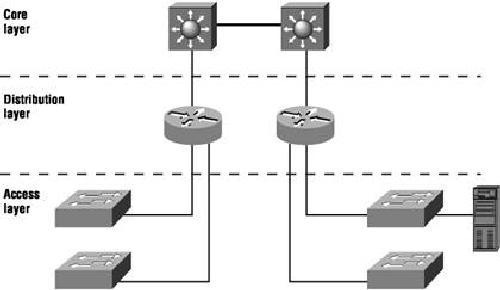
Understanding the Cisco Three-Layer Hierarchical Model
Understanding the Cisco Three-Layer Hierarchical Model Hierachical network design helps us to make networks more reliable and predictable. Level by level design help to understand networking factions easily like, we can use tools like access lists at specific level and can avoid them from others. Cisco layer model consist of the following three layers. The …