Cryptology
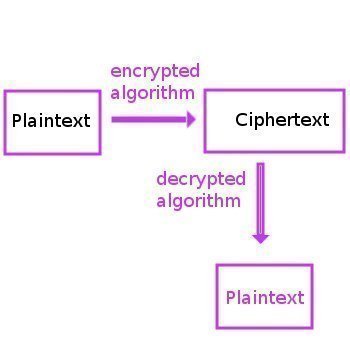
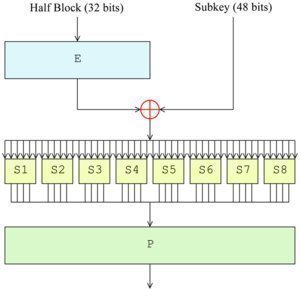
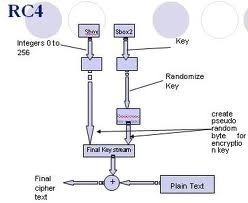
The field of cryptology includes both the study of and practice of securing information in the presence of untrusted third parties or adversaries. Specifically, it is focused on creating and analyzing the protocols used to subvert attempts by adversaries to gain access to or interrupt the flow of information between trusted parties. Specific focus areas …