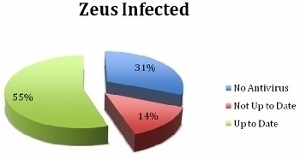
One-Time Pad
A one-time pad is a form of encryption that is difficult to decipher or crack if one is not the intended recipient. If done correctly, the strength of encryption of plaintext can almost be impossible to break in a useful timeframe. The system takes each character from plaintext and uses modular addition with a character …