Certificate Authority
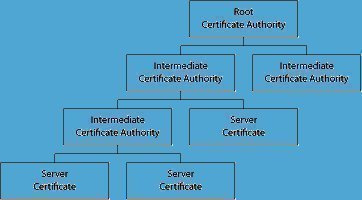
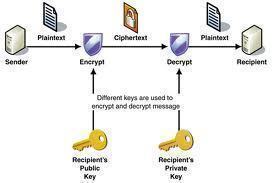
Certificate Authority or Certification Authority (CA) is an entity, which is core to many PKI (Public Key Infrastructure) schemes, whose purpose is to issue digital certificates to use by other parties. It exemplifies a trusted third party. Some certification authorities may charge a fee for their service while some other CAs are free. It is …