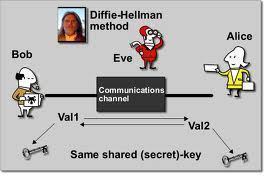
Diffie-Hellman
The Diffie-Hellman key exchange was first published by Whitfield Diffie and Martin Hellman in 1976 and is a popular method for exchanging cryptographic keys. The method is one of the most straight-forward examples of key exchanges implemented in the cryptology field and allows two individuals or parties that have not worked together before to establish …