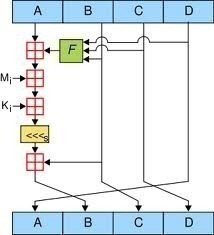
MD5 (Message Digest 5)
MD5 is a message digest algorithm. MD5 takes a variable length input and produces a 128-bit message digest. MD5 was designed by Ron Rivest in 1991. MD5 is officially defined in RFC 1321 – The MD5 Message-Digest Algorithm. MD5 Usage MD5 is used in many applications, including GPG, Kerberos, TLS / SSL, Cisco type 5 …