In the Windows NT domain model, domains had to be bound together through trust relationships simply because the SAM databases used in those domains could not be joined. What this meant was that where a domain trusted another Windows NT domain, the members of the domain could access network resources located in the other domain. Defining trust relationships between domains eliminates the need for an Administrator to configure user accounts in multiple domains.
In a trust relationship, the two domains are referred to as the trusting domain and the trusted domain. The trusted domain is the domain where the trust relationship is created. The trusting domain is the other domain specified in the trust, that is, the one wherein network resources can to be accessed. The trusting domain in this case recognizes the logon authentications of the trusted domain. The NT LanMan Challenge Response supports the logon trust relationship. This allows pass-through authentication of users from the trusted domain. One of the shortfalls of Windows NT trust relationships is that trusts between domains were one way and non-transitive. This meant that the defined trust relationship ended with the two domains between which the particular trust was created. The rights implicit in the trust relationship also flowed only in one direction. Because of this, defining and managing trust relationships in the Windows NT domain structure was a cumbersome and labor intensive task. The Windows NT domain worked well in small enterprises where one domain typically existed in the enterprise. In those larger enterprises that have multiple domains, Administrators have to define trust relationships between the domains in order for a user in one domain to access resources in another domain.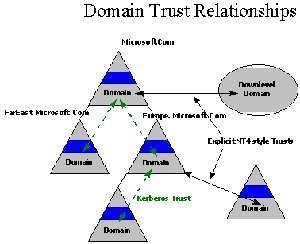
In Windows 2000 and Windows 2003, Active Directory is built on the concept of trust relationships between domains. Although the actual concept of trust relationships is not new in Windows Server 2003, there are new trust capabilities and trust types available for Windows Server 2003 Active Directory domains.
In Windows Server 2003, authentication of users or applications occurs through the use of one of the following trust protocols:
- NT LAN Manager (NTLM) protocol: This protocol is used when one of the computers in the trust relationship does not support the Kerberos version 5 protocol.
- The Kerberos version 5 protocol is the default trust protocol used when computers in trust relationships are running Windows Server 2003.
The characteristics of Windows Server 2003 trusts are outlined below:
- Trusts can be non-transitive or transitive:
- Transitive trusts: With transitive trusts, trust is applicable for each trusted domain. What this means is where Domain1 trusts Domain2, and Domain2 trusts Domain3, Domain1 would also trust Domain3.
- Non-transitive trust: The defined trust relationship ends with the two domains between which the particular trust is created.
- Trusts can be one way or two way:
- One way trusts: Based on the direction of the trust, one way trust can further be broken into either incoming trust or outgoing trusts. One way trust can be transitive or non-transitive:
- Incoming Trust: With incoming trust, the trust is created in the trusted domain and users in the trusted domain are able to access network resources in the trusting domain or other domain. Users in the other domain cannot however access network resources in the trusted domain.
- Outgoing Trust: In this case, users in the other domain can access network resources in the initiating domain. Users in the initiating domain are not able to access any resources in the other domain.
- Two way trusts: A two way trust relationship means that where Domain1 trusts Domain2, then Domain2 trusts Domain1. The trust basically works both ways and users in each domain are able to access network resources in either one of the domains. A two way, transitive trust relationship is the trust that exists between parent domains and child domains in a domain tree. In two way transitive trust, where Domain1 trusts Domain2 and Domain2 trusts Domain3, then Domain1 would trust Domain3 and Domain3 would trust Domain1.Two way transitive trust is the default trust relationship between domains in a tree. It is automatically created and exists between top level domains in a forest.
- One way trusts: Based on the direction of the trust, one way trust can further be broken into either incoming trust or outgoing trusts. One way trust can be transitive or non-transitive:
- Trusts can be implicit or explicit trusts:
- Implicit: Automatically created trust relationships are called implicit trust. An example of implicit trust is the two way transitive trust relationship that Active Directory creates between a parent and child domains.
- Explicit: Manually created trust relationships are referred to as explicit trust.
Window Server 2003 Active Directory Forest Trust Capability
Forest trust is a new feature introduced with Windows Server 2003 Active Directory. To better understand the feature, first look at how forest trust was established in the Windows NT and Windows 2000 domain structures. In these domain structures, when users located in one forest needed to access resources located in a different forest, an external trust relationship had to be defined between the two domains. External trusts are one-way and non-transitive in nature. This in turn increases the Administrative effort required to create and maintain the external trusts needed to enable forest trust in the Windows NT and Windows 2000 domain structures. Forest trust on the other hand enables the user to create two way trust relationships between all domains in two forests. The number of external trusts that has to be configured in Windows NT and Windows 2000 domain structures is reduced in Windows Server 2003 Active Directory domains. The trust between the Active Directory forests is transitive in nature.
Types of Active Directory Trust Relationships
The types of trust relationships that can be created and configured for Active Directory domains are discussed in this section. As an Administrator for Active Directory Windows Server 2003 domains, it is important to understand the different types of trusts that are supported in Windows Server 2003 and to know which trust relationship to create for the different network resource access requirements that exist within the organization.
- Tree-root trust: Tree root trust is automatically/implicitly created when a new tree root domain is added to a forest. The trust relationship exists between two root domains within the same forest. For instance, if there is an existing forest root domain, and a new tree root domain is added to the same forest, tree root trust is formed between the new tree root domain and the existing forest root domain. Tree root trust is transitive and two way.
- Parent-child trust: Parent-child trust is implicitly established when new child domains are added to a domain tree. Parent-child trust is a two-way, transitive trust relationship. Active Directory automatically creates a trust relationship between the new child domain and the domain directly above it in the domain namespace hierarchy. What this means is that the trust relationship exists between those domains that have a common contiguous DNS namespace and who are part of the same forest. Parent-child trust enables child domain authentication requests to be passed through the parent domain for authentication. In addition, when a new domain is added to the tree, trust relationships are created with each domain in the tree. This means that network resources in the tree’s individual domains can be accessed by all other domains in the tree.
- Shortcut trust: An administrator explicitly creates a shortcut trust and is either a one way transitive trust or two way transitive trust. Shortcut trust is usually created when users want to speed up or enhance authentication performance between two domains in different trees but within the same forest. One way shortcut trust should be created when users in Domain1 need to access Active Directory objects in Domain2 but users in Domain2 do not need to access objects in Domain1. Two way shortcut trust should be created when users in each domain need to access objects in each other’s domain.
- Realm trust: An administrator explicitly creates realm trust and it can be defined as either a transitive or non-transitive trust. It can also either be a one way or two way trust. Realm trust enables users to create a trust relationship between a Windows Server 2003 Active Directory domain and a non-Windows Kerberos version 5 realm. Realm trust therefore facilitates interoperability between a Windows Server 2003 domain and a realm used in Kerberos version 5 implementations.
- External trust: An administrator explicitly defines the external trust to enable trust between domains that are located in different forests and to create trust between an Active Directory domain and a down-level Windows NT 4 domain. External trust is always non-transitive but can be either one-way trusts or two-way trusts. External trust is usually only created in Windows Server 2003 Active Directory environments when users need to access network resources in a domain that resides in a different forest and forest trust cannot be created between the two domains. When external trust is created between an Active Directory domain and a down-level Windows NT 4 domain, it is a one-way, non-transitive trust relationship.
- Forest trust: An Administrator explicitly created Forest trust to enable trust between two Active Directory forests. Forest trust is transitive in nature and can either be one-way or two-way. Forest trust is only available in Windows Server 2003. Before users can create forest trust between two forests, each domain in the particular forest and each forest has to be raised to and run at the Windows Server 2003 functional level. Because forest trust is created between two root domains of two forests, it can create two way trusts with each domain within the two forests. This basically means that users would be able to access Active Directory objects between all domains encompassed by the particular forest trust relationship.
Planning Considerations for Trust Relationships
Tree root trust and Parent-child trust are implicitly created by Active Directory when new domains are created. What this means is that users do not need to explicitly create these trusts nor do they have to perform any configuration or management tasks for the trust relationships.
Shortcut trust, Realm trust, External trust, and Forest trust differ from Tree root and Parent-child trust in that the former four trusts have to be explicitly created and managed. Because of the different types of trust relationships that can be created, users need to plan which type of trust relationship to create for the domains within their Active Directory environment.
Shortcut Trust
Before any shortcut trusts can be created, users must be a member of the Enterprise Admin or Domain Admin groups in each domain in the forest. Another requirement is that the domains are creating shortcut trust for Windows Server 2003 domains that reside in the same forest. As mentioned earlier, Shortcut trust is usually created to speed up authentication between two domains in different trees but within the same forest. Shortcut trust can be a one way transitive trust or two way transitive trust. What shortcut trust essentially does is it shortens the trust path traversed for authentication requests made between domains of different trees. Shortcut trust is typically configured in an intricate forest where users continually need to access resources of domains belonging to different trees. Shortcut trust improves query response performance as well.
- Users would need to create one way shortcut trust when the optimized trust path is only needed for one of the domains in the trust. The other domain’s users would need to transverse the full trust path when handling authentication requests.
- Users would need to create two way shortcut trust when the users in each domain need to use the shortened trust path for authentication requests.
The Active Directory tool used to create shortcut trust is the Active Directory Domains and Trusts console. The console enables users to specify selective authentication for incoming shortcut trust and outgoing shortcut trust. What this means is that users can set authentication differently for the two forms of trust. When users set selective authentication for incoming shortcut trust, they would need to specify permissions for every resource that users in the other domain should be able to access. If domain wide authentication is specified on the incoming shortcut trust, users in the other domain and users in the local domain have the identical permissions to network resources.
Realm Trust
In order to create realm trust, users should have Enterprise Admin or Domain Admin permissions for the Windows Server 2003 domain and should have the permissions required for the non-Windows Kerberos version 5 realm. Users would typically create realm trust to enable trust between a Windows Server 2003 domain and a MIT or Unix v5 Kerberos realm. Users can create Realm trust as either transitive or non-transitive trust and as either one way or two-way trust.
External Trust
Users need to be a member of Enterprise Admins or Domain Admins of the Windows Server 2003 domain and Enterprise Admins or Domain Admins of the other domain to create one way or two way External trust.
Recall from an earlier discussion, that External trust is always non-transitive in nature, and is typically used to enable trust between an Active Directory domain and a down-level Windows NT 4 domain. When the External trust is created, security principals (Users, Groups, Computers) from the external domain are able to access network resources in the internal domain (Windows Server 2003 domain). The foreign security principals can be examined in the Active Directory Users And Computers console. The only requirement is that Advanced Features are enabled. Users can explicitly define different authentication for incoming External trusts and outgoing External trusts.
Forest Trust
Users need to belong to the Enterprise Admins groups in each forest that they want to create forest trust between. In addition to this, the domains within each forest and each particular forest have to be raised to the Windows Server 2003 functional level.
Forest trust is typically created when enterprises mergers or takeovers occur and each company within the enterprise still needs to maintain some form of administrative independence. This trust relationship enables users to access Active Directory objects between all domains impacted by the particular forest trust relationship. Forest trust is transitive and can be one way or two way trust. Users would create one way Forest trusts when users in the trusted forest need to access Active Directory objects in the trusting forest, but those users in the trusting forest do not need to access resources in the trusted forest. Users would create two way Forest trust in cases where users in either one of the forests need to access resources hosted in the other forest.
How to Create Shortcut Trust with Active Directory Domains and Trusts
- Open the Active Directory Domains and Trusts console.
- In the console tree, locate and right click the domain for which the Shortcut trust should be configured and click Properties from the shortcut menu.
- When the chosen domain’s Properties dialog box opens, click the Trusts tab.
- Click the New Trust button at the bottom of the dialog box.
- This action starts the New Trust Wizard.
- Click Next on the Welcome To The New Trust Wizad page.
- When the Trust Name page opens, enter the DNS name of the other domain to create the trust with. Click Next.
- On the Direction Of Trust page, select one of the following options:
- Two-Way: Click this option to define two way Shortcut trust. This would mean that users in each domain would be able to access resources in both domains.
- One-Way: Incoming: This option should be enabled to only allow users of this particular domain to be able to access resources in the other domain.
- One-Way: Outgoing: This option should be selected to allow users of the other domain to be able to access resources in this particular domain. Click Next.
- When the Sides Of Trust page opens, select one of these options:
- This Domain Only: Selecting this option creates the Shortcut trust in the local domain.
- ” Both This Domain And The Specified Domain:” Selecting this option creates the Shortcut trust in the local domain and in the other domain that you indicated. Click Next
- The New Trust Wizard displays different pages next, based on what was selected in the previous two steps.
- Where Two-Way or One-Way: Outgoing was selected in Step 8,and This Domain Only was selected in Step 9, the wizard displays the Outgoing Trust Authentication Level page. Select either Domain Wide Authentication or Selective Authentication. Choosing Domain Wide Authentication results in the automatic authentication of users in the other domain for network resources in the local domain. If Selective Authentication was selected, the users in the other domain are not automatically authenticated for resources in the local domain. Click Next. The wizard then displays the Trust Password page. This is where users have to set the password for the trust. Click Next.
- Where One-Way: Incoming was selected in Step 8 and This Domain Only was selected in Step 9, the wizard displays the Trust Password page. Enter the password for the trust in the boxes. Click Next.
- Where Both This Domain And The Specified Domain was selected in Step 9, the wizard displays the User Name And Password page. Users have to provide the user name and password of an Administrator account that has the necessary rights in the other domain. Click Next.
- The Trust Selections Complete page is displayed next. All the settings previously specified are shown on this page. After checking that the configuration settings are correct, click Next.
- The New Trust Wizard now creates the shortcut trust relationship.
- When the Trust Creation Complete page appears, click Next.
- The Confirm Outgoing Trust page allows users to verify outgoing trust. Click Yes, Confirm The Outgoing Trust, or click No. Do Not Confirm The Outgoing Trust. Click Next.
- The Confirm Incoming Trust page allows users to verify incoming trust. Click Yes, Confirm The Incoming Trust, or click No. Do Not Confirm The Incoming Trust. Click Next.
- Click Finish when the Completing The New Trust Wizard page is displayed.
How to Create Realm Trust with Active Directory Domains and Trusts
- Open the Active Directory Domains and Trusts console.
- In the console tree, locate and right click the domain for which Realm trust will be configured, and click Properties from the shortcut menu.
- When the Properties dialog box of the domain opens, click the Trusts tab.
- Click the New Trust button at the bottom of the dialog box.
- Click Next on the Welcome To The New Trust Wizard page.
- When the Trust Name page opens, enter the DNS name of the other domain for the realm trust. Click Next.
- The Trust Type page appears next. Select Realm Trust. Click Next.
- When the Transitivity Of Trust page opens, select one of the following options:
- Nontransitive: Select this option if the Realm trust should end with the two domains between which it is created.
- Transitive: Select this option if this particular domain is wanted and all other trusted domains to create trust with the realm and other trusted realms. Click Next.
- On the Direction Of Trust page, select one of the following options:
- Two-Way: Click this option in order to define two-way Realm trust. This would mean that users in the domain and realm would be able to access resources in both the domain and realm.
- One-Way: Incoming: This option should be enabled to only allow users of this particular domain to be able to access resources in the realm.
- One-Way: Outgoing: This option should be selected to only allow users of realm to be able to access resources in this particular domain. Click Next.
- The wizard displays the Trust Password page next. Enter the password for the trust in the boxes. Click Next.
- The Trust Selections Complete page is displayed next. All the settings previously specified are shown on this page. After checking that the configuration settings are correct, click Next.
- The New Trust Wizard creates the Realm trust relationship.
- Click Finish on the Completing The New Trust Wizard page.
How to Create External Trust with Active Directory Domains and Trusts
Users first have to specify a DNS forwarder for each of the DNS servers that are authoritative for the trusting forests.
Use the DNS Administration tool to configure DNS forwarders.
- Click Start, click Administrative Tools, and click DNS.
- Right-click the DNS server and click Properties from the shortcut menu.
- When the DNS server’s Properties dialog box opens, click the Forwarders tab.
- Click New and enter the DNS domain name that needs queries to be forwarded.
- In the Selected Domain’s IP Address List, enter the IP addresses of the servers to which these queries are forwarded.
- Click Add.
- Click OK.
- Open the Active Directory Domains and Trusts console.
- In the console tree, locate and right-click the domain in the initial forest to configure External trust and click Properties from the shortcut menu.
- When the domain’s Properties dialog box opens, click the Trusts tab.
- Click the New Trust button at the bottom of the dialog box.
- Click Next on the Welcome To The New Trust Wizard page.
- When the Trust Name page opens, enter the DNS name of the domain in the other forest. Click Next.
- The Trust Type page appears next if the forest functional level is raised to Windows Server 2003 forest functional level. Select the External Trust option. Click Next.
- The Direction Of Trust page is displayed straight after the Trust Name page if the forest functional level is not raised to Windows Server 2003. Select one of the following options:
- Two-Way: Click this option in order to define two way External trust. This would mean that users in each domain would be able to access resources in both domains.
- One-Way: Incoming: This option should be enabled only to allow users of this particular domain to be able to access resources in the other domain.
- One-Way: Outgoing: This option should be selected only to allow users of the other domain to be able to access resources in this particular domain. Click Next.
- When the Sides Of Trust opens, select one of these options:
- This Domain Only: Selecting this option creates the trust in the local domain.
- Both This Domain And The Specified Domain: Selecting this option creates the trust in the local domain and in the other domain. Click Next
- The New Trust Wizard displays different pages next, based on what was selected in the previous two steps.
- Where Two-Way or One-Way: Outgoing was selected in Step 8 and This Domain Only was selected in Step 9, the wizard displays the Outgoing Trust Authentication Level page. Select either Domain Wide Authentication or Selective Authentication. Choosing Domain Wide Authentication results in the automatic authentication of users in the other domain for network resources in the local domain. If Selective Authentication is selected, the users in the other domain are not automatically authenticated for resources in the local domain. Click Next. The wizard then displays the Trust Password page. This is where users have to set the password for the trust. Click Next.
- Where One-Way: Incoming was selected in Step 8 and This Domain Only was selected in Step 9, the wizard displays the Trust Password page. Enter the password for the trust. Click Next.
- Where Both This Domain And The Specified Domain was selected in Step 9, the wizard displays the User Name And Password page. The user must provide the user name and password of an Administrator account that has the necessary rights. Click Next.
- When the Trust Selections Complete page is displayed, the settings previously specified are shown. After checking that the configuration settings are correct, click Next.
- The New Trust Wizard now creates the External trust.
- When the Trust Creation Complete page appears, click Next.
- The Confirm Outgoing Trust page allows users to verify outgoing trust. Click Yes, Confirm The Outgoing Trust, or click No. Do Not Confirm The Outgoing Trust. Click Next.
- The Confirm Incoming Trust page allows users to verify incoming trust. Click Yes, Confirm The Incoming Trust, or click No. Do Not Confirm The Incoming Trust. Click Next.
- Click Finish.
How to Create Forest Trust with Active Directory Domains and Trusts
Specify a DNS forwarder for each of the DNS servers that are authoritative for the trusting forests before being able to use the Active Directory Domains and Trusts console to create Forest trust relationships. Use the DNS Administration Tool to configure the necessary DNS forwarder. In addition to this, ensure that the forest functional level for each forest is set to Windows Server 2003 forest functional level.
- Open the Active Directory Domains and Trusts console.
- In the console tree, locate and right-click the domain in the initial forest that Forest trust should be configured for and click Properties from the shortcut menu.
- When the domain’s Properties dialog box opens, click the Trusts tab then click the New Trust button.
- In the Welcome To The New Trust Wizard page, click Next.
- Enter the DNS name of the domain in the other forest on the Trust Name page. Click Next.
- In the Trust Type page, select the Forest Trust option. Click Next.
- On the Direction Of Trust page select one of the following options:
- Two-Way: Click this option in order to define two way Forest trust. This would mean that users in each forest would be able to access resources in both forests.
- One-Way: Incoming: This option should be enabled only to allow users of this particular forest to access resources in the other forest.
- One-Way: Outgoing: This option should be selected only to allow users of the other forest to access resources in this particular forest. Click Next.
- When the Sides Of Trust opens, select one of these options:
- This Domain Only: Selecting this option creates the trust in the local forest.
- Both This Domain And The Specified Domain: Selecting this option creates the trust in the local forest and in the other forest. Click Next.
- Where Two-Way or One-Way: Outgoing was selected in Step 7 and This Domain Only was selected in Step 8, the wizard displays the Outgoing Trust Authentication Level page. Select either Domain Wide Authentication or Selective Authentication. Choosing Domain Wide Authentication results in the automatic authentication of users in the other forest for network resources in the local forest. If Selective Authentication is specified, the users in the other forest are not automatically authenticated for resources in the local forest. Click Next. The wizard then displays the Trust Password page. This is where users have to set the password for the trust. Click Next.
- Where One-Way: Incoming was selected in Step 7 and This Domain Only was selected in Step 8, the wizard displays the Trust Password page. Enter the password for the trust. Click Next.
- Where Both This Domain And The Specified Domain was selected in Step 8, the wizard displays the User Name And Password page. The user must provide the user name and password of an Administrator account that has the necessary rights. Click Next.
- When the Trust Selections Complete page is displayed, the settings previously specified are shown. After checking that the configuration settings are correct, click Next.
- The New Trust Wizard now creates the Forest trust.
- When the Trust Creation Complete page appears, click Next.
- The Confirm Outgoing Trust page allows users to verify outgoing trust. Click Yes, Confirm The Outgoing Trust or click No. Do Not Confirm The Outgoing Trust. Click Next.
- The Confirm Incoming Trust page allows users to verify incoming trust. Click Yes, Confirm The Incoming Trust or click No. Do Not Confirm The Incoming Trust. Click Next.
- Click Finish on the Completing The New Trust Wizard page.
How to Remove Existing Active Directory Trust Relationships
- Open the Active Directory Domains And Trusts console.
- In the console tree, right-click a domain that is specified in the trust relationship to be removed and select Properties from the shortcut menu.
- Click the Trusts tab.
- Use the Domains Trusted By This Domain (Outgoing Trusts) box to select the trust to be removed.
- Click the Remove button alongside the box.
- In order to remove the trust from the local domain only, click the No, Remove The Trust From The Local Domain Only option, and click OK.
- In order to remove the trust from the local domain and the other domain, click the Yes, Remove The Trust From Both The Local Domain And The Other Domain option. Enter the appropriate user name and password combination in the User Name and Password boxes and click OK.
- Click Yes to verify the desire to remove the trust relationship.
- Use the Domains That Trust This Domain (Incoming Trusts) box to select the trust to be removed.
- Choose the appropriate option in the Active Directory dialog box and click OK.
- Click Yes to verify the desire to remove the trust relationship.
How to Validate Existing Active Directory Trust Relationships
- Open the Active Directory Domains And Trusts console.
- In the console tree, right click a domain that is defined in the trust relationship to be validated and select Properties from the shortcut menu.
- Click the Trusts tab.
- Select the trust to be examined in one of the following boxes:
- Domains Trusted By This Domain (Outgoing Trusts) box
- Domains That Trust This Domain (Incoming Trusts) box
- After the trust is selected, click the Properties button.
- When the trust’s Properties dialog box opens, click the Validate button.
- In order to verify outgoing trust, click the No, Do Not Validate The Incoming Trust option and click OK.
- In order to verify incoming trust and outgoing trust, click Yes, Validate The Incoming Trust option. Enter the appropriate user name and password combination in the User Name and Password boxes and click OK.
- After the trust is validated, a message is displayed indicating this.
- Click OK.
How to Create and Manage Trust Relationships with the Windows Domain Manager Command-line Tool
Users can use the Windows Domain Manager command line tool to create and manage Active Directory trusts. Netdom.exe is included with the Windows Support Tools available on the Windows Server 2003 Setup CD-ROM.
The netdom trust command creates and manage trusts:
netdom trust TrustingDomainName /d: TrustedDomainName [/ud:[Domain]User]
[/pd:{Password|*}] [/uo: User] [/po:{Password|*}] [/verify] [/reset] [/passwordt: NewRealmTrustPassword]
[/add [/realm]] [/remove [/force]] [/twoway] [/kerberos] [/transitive[:{YES|NO}]] [/verbose]
- TrustingDomainName indicates the name of the trusting domain.
- /d: TrustedDomainName indicates the name of the trusted domain. If this parameter is not specified, the domain to which this computer is a member of is utilized.
- /ud:[Domain]User indicates the user account that should be used. If this parameter is not specified, the current user account is used.
- /pd:{Password|*} indicates the password associated with the user account.
- /verify verifies the trust password for a particular trust
- /reset resets the trust password for trusted domains
- /passwordt: NewRealmTrustPassword defines the trust password for the Windows domain if a non-Windows Kerberos realm is defined.
- /add indicates that a trust relationship should be created
- /realm defines the trust as being created with a non-Windows Kerberos realm
- /remove indicates that the trust relationship should be removed
- /force indicates that the trusted domain object as well as the cross-reference object for the other domain should be removed.
- /twoway indicates that two way trust should be created.
- /kerberos indicates that the trust protocol should be the Kerberos protocol.
- /transitive[:{YES|NO}] indicates whether trust should be created as transitive or non-transitive trust.
- /verbose indicates verbose output should be displayed.

Andrew
Hi,
Any advice on how to police a trust relationship between two forests? Specifically, to ensure that a one way trust REMAINS a one way trust in a specified direction.
I remember that ISA firewall could do this (application aware etc)…, but not sure about the latest product. There do not appear to be any CISCO etc firewalls that can do this either – that I can find.
Is it possible to enforce a one way trust through firewall rules?
Any help gratefully received!
Regards
Andrew
Bernie
How do you establish trusts for individuals in one domain to another domain w/o having to trust all the users in the original domain?
shadab ahmad
Hi ,
How to trouble shoot Broken Tree Root Trust