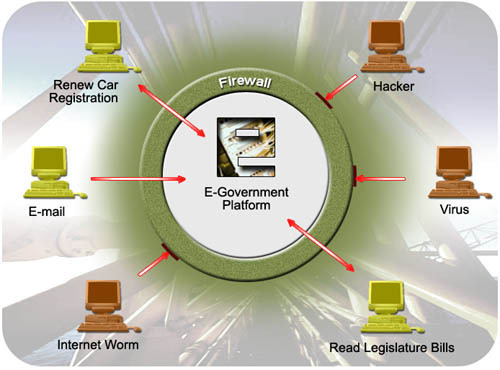
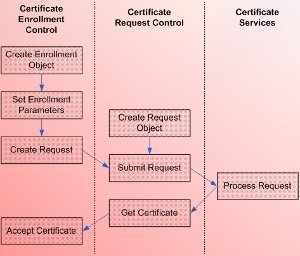
How Firewall Protection Works
Firewall protection works by blocking certain types of traffic between a source and a destination. All network traffic has a source, a destination, and a protocol. This protocol is usually TCP, UDP, or ICMP. If this protocol is TCP or UDP, there is a source port and a destination port. Most often the source port …