How to Monitor CPU Temperature
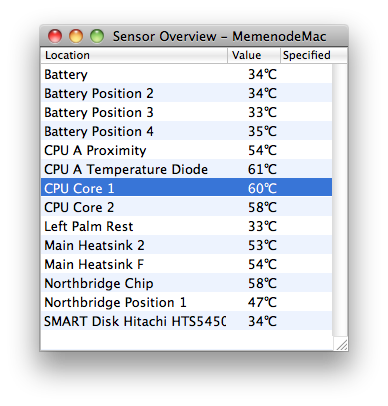
Excessive heat damages electronics. Monitoring CPU and other computer components’ temperature help them run properly. To make the most of monitoring software, users must ensure that ACPI functionality is enabled in their motherboard BIOS. Why CPU Temperature is so Important When the first affordable PCs were offered to the general public in the early 80’s, …