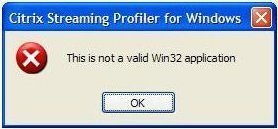
Not a Valid Win32 Application
The Not a valid Win32 application error message may occur in a number of different scenarios. This indicates that an executable file, application, or program is not able to communicate correctly with the Windows API. The error may occur during or after the installation of an application, program, or in certain cases – hardware. The …