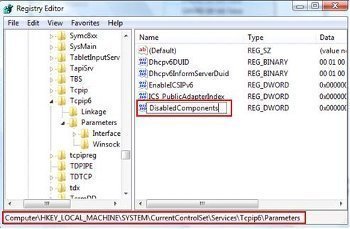
How to Remove IPv6 in Windows
IPv6 stands for Internet Protocol version 6. IPv6 is the latest version of the network-layer protocol for packet-switched networks. The version that is generally used is IPv4. One of the reasons for the upgrade to IPv6 is that it allows greater space and flexibility in assigning IP addresses. For instance, IPv4 is based on a …