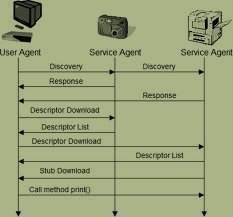
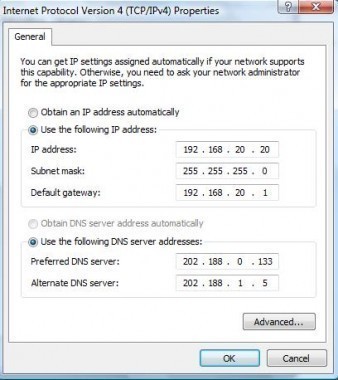
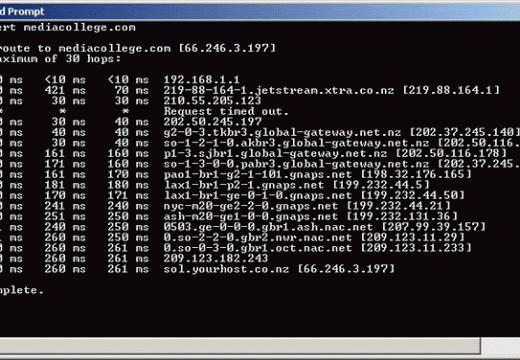
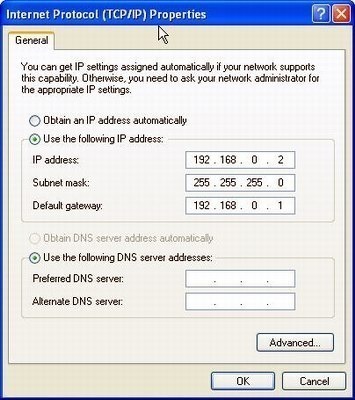
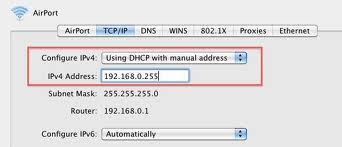
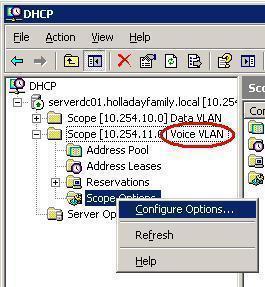
What is a Zeroconf?
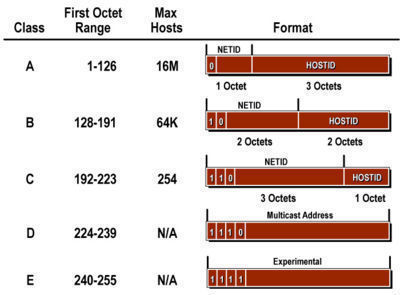
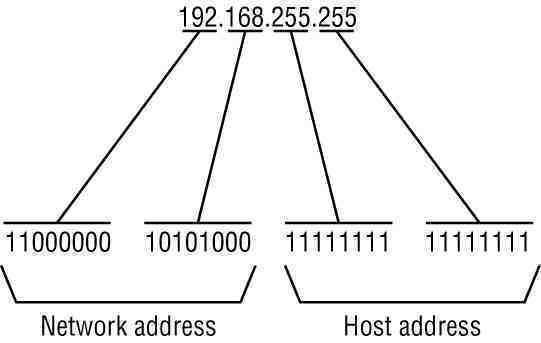
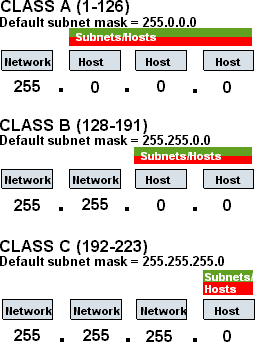
Zeroconf (zero configuration networking) refers to several protocols and techniques that are used together to create an IP (Internet Protocol) network with no special configuration servers or manual operator intervention. These networks allow novices to connect computers, network devices, scanners, and printers to create a functioning network without requiring manual configuration. Zeroconf does not require …