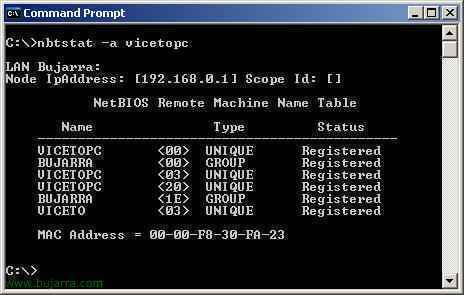
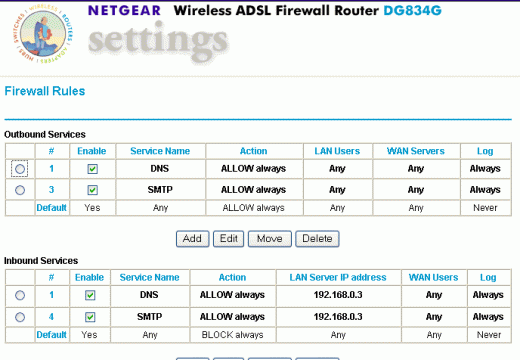
How to Block an IP Address
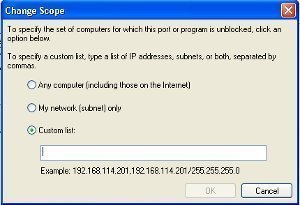
An IP address is the numeric label or sequence of numbers that is assigned to a computer or device used on the Internet or a local area network. It is a means of identification and determining the user's address online. When an IP address is blocked, network connections to or from that address are not …